


Ransomware, like no other threat, puts fear into the hearts and minds of data administrators. From small businesses to hospitals and critical infrastructure, organizations of all sizes have been victims of ransomware in recent years. Sadly, ransomware protection is more a buzzword than a single product or solution.
The cybersecurity vendors doing the most for clients in addressing ransomware are a list of familiar and emerging security tools and software for malware detection and response. Beyond next-generation antivirus, backup, and recovery features, increasing protection across the security architecture is essential to combating ransomware.
Read on to learn more about ransomware protection, the best vendors on the market, how products compare, and what to consider when evaluating solutions.
| Vendor | Cloud | On-Premises | Backup | Disaster Recovery | Email Security | DLP | Patch Mgmt | Firewall | Sandbox | Windows | Linux |
| Acronis | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | 🚫 | ✅ | ✅ | ✅ |
| Avast | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| AVG | ✅ | ✅ | ✅ | 🚫 | ✅ | ✅ | ✅ | ✅ | 🚫 | ✅ | ✅ |
| Bitdefender | ✅ | ✅ | ✅ | ✅ | ✅ | 🚫 | ✅ | ✅ | ✅ | ✅ | ✅ |
| Check Point | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| ESET | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| Kaspersky | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| Malwarebytes | ✅ | ✅ | ✅ | ✅ | 🚫 | 🚫 | ✅ | 🚫 | ✅ | ✅ | ✅ |
| Sophos | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| Trend Micro | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |

Acronis offers cybersecurity solutions to service providers, businesses, and individuals, bolstering their security posture and guarding against ransomware.
Acronis Cyber Protect includes advanced security features like exploit prevention, URL filtering, and anti-malware to extend protection to web browsing, the recovery process, and backed-up data. Components included in Acronis’ stack solution include data loss prevention (DLP), email security, disaster recovery, and backups.
Pros
Cons

Avast is an antivirus and internet security vendor offering protection solutions for home offices, small businesses, and channel partners like managed service providers (MSP). For up to 100 devices, Avast’s business subscriptions include an online management platform, device malware protection, and IT support via call, email, or webchat. Avast’s additional security products include advanced remote control, antivirus for Linux, and patch management.
Pros
Cons
AVG is another antivirus company specializing in malware protection across operating systems and business products for file servers, email servers, patch management, and internet security. Ideal for small businesses, the AVG Antivirus subscriptions offer a cloud console for remote management and protection, dubbed “Shields,” for web traffic, email, files, and suspicious behavior.
The AVG Internet Security Business edition goes a tad farther, offering protection for Microsoft Exchange and password protection for Chrome and Firefox browsers.
Pros
Cons

Bitdefender is an undisputed industry leader for ransomware protection, as the cybersecurity vendor offers a range of tools for endpoint protection and securing servers, containers, email, and mobile devices. Bitdefender’s endpoint detection and response (EDR) capabilities offer customers root cause analysis, incident visualization, and ransomware mitigation through a real-time backup of files before suspicious modifications.
Bitdefender GravityZone has a comprehensive stack of features to protect hybrid endpoints, and add-ons for additional client needs with options for small businesses, medium-to-large businesses, and MSPs.
Pros
Cons
Read more: Top Server Backup Software & Solutions

Firewall pioneer Check Point Software Technologies is an end-to-end cybersecurity solutions provider. The company’s unified security solution is Check Point Infinity, made up of Harmony for secure access control, CloudGuard to secure cloud workloads, and Quantum to defend data centers and enterprise network security. Infinity-Vision combines Check Point’s three decades of experience and expertise into a holistic infrastructure protection plan.
Pros
Cons

ESET is a veteran antivirus and internet security vendor offering malware protection to individuals, businesses, and channel partners. For small to medium companies, ESET PROTECT offers clients on-premises or cloud security management, hybrid endpoint protection, and real-time protection for all data passing through general file servers.
Clients working with various devices and operating systems will benefit from ESET’s support for Windows, macOS, and Linux infrastructure as well as iOS and Android mobile devices.
Pros
Cons

Kaspersky is a comprehensive internet security vendor with solutions for individuals, small and medium businesses, and enterprise organizations with over 1,000 employees. From protecting the home office to global data centers, Kaspersky’s stack of cybersecurity products addresses data, endpoint, and network protection.
For enterprise IT environments, the veteran solution provider offers advanced EDR capabilities and additional security products for hybrid cloud workloads, embedded systems, internet gateways, and Microsoft Office 365.
Pros
Cons
Also read: Best Cloud & Online Backup Services

Malwarebytes is an anti-malware software company offering consumers, businesses, and channel partners affordable subscriptions to its next-generation antivirus and endpoint protection solutions.
Ideal for small to medium companies, Malwarebytes’ solution includes a cloud management console, threat isolation, and forensics for Windows and Linux servers. The company’s business solution, Malwarebytes Endpoint Protection, is available for servers and teams up to 100+ devices.
Pros
Cons

Sophos is an established network security leader with endpoint protection, managed detection and response, and next-generation firewalls leading its solution stack. Whether it’s on-premises, cloud, or virtual workloads, Intercept X for Servers has advanced features to defend against the latest threats.
As an EDR solution, clients benefit from Sophos advancements in extended detection and response (XDR), orchestrating a comprehensive security system model.
Pros
Cons

Next to Check Point, Trend Micro offers the most comprehensive portfolio of cybersecurity products for individual users up to enterprise networks. Its suite of solutions includes XDR capabilities, zero trust insights, email security, and a handful of tools for securing hybrid cloud infrastructure.
For network defense, Trend Micro’s intrusion prevention system (IPS), global threat intelligence, and advanced threat detection all aid administrators in actively blocking inbound, outbound, and lateral attacks.
Pros
Cons
Read more: Best Server Virtualization Software
Ransomware is an advanced malware strain where a threat actor encrypts entire segments of an IT environment and holds data hostage at an often steep price. Ransomware threat actors often use data exfiltration to harbor an organization’s data for extended periods.
This power to extort the organization again, or release proprietary and sensitive data to the public, can lead to long-term costs or reputational damage.
Read more on eSecurity Planet: How to Prevent Ransomware Attacks: 20 Best Practices
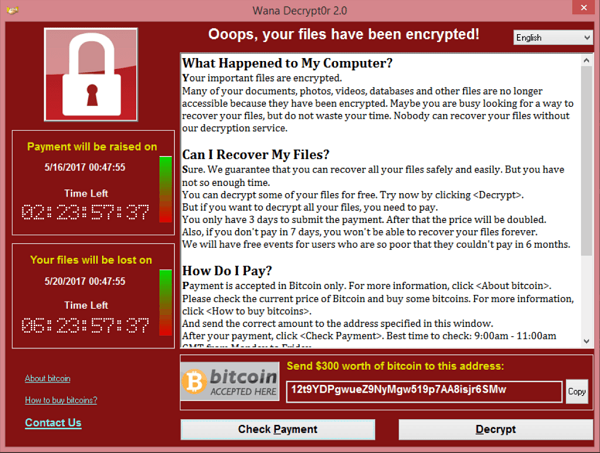
Protecting against ransomware means developing a cybersecurity model equipped to fend off common and advanced malware strains — and when the worst happens, having the necessary backups to recover from data loss due to encryption. Guarding against future threats also means conducting proper forensic analysis of past disruptions and existing vulnerabilities.
Critical tools and best practices for ransomware protection include:
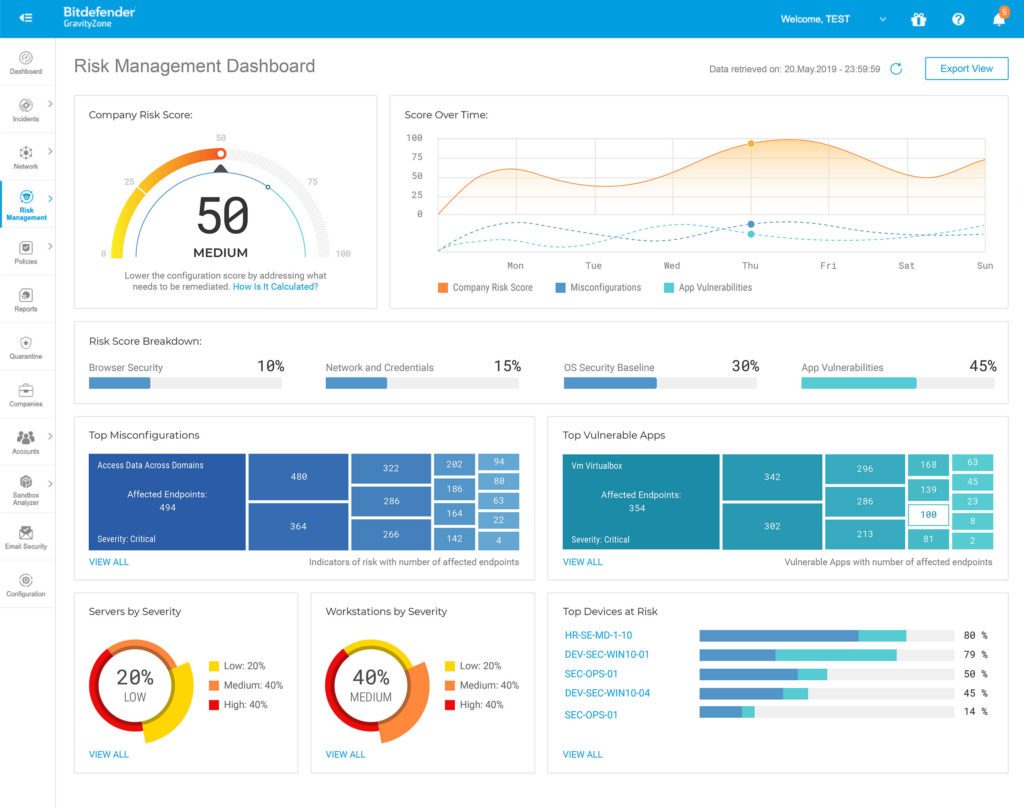
Ransomware protection is about much more than a single product or solution. Organizations should consider the above tools part of the jigsaw puzzle, rather than inclusive ransomware protection. The best so-called ransomware protection solutions are those efficiently securing users, applications, and network segments from advanced malware threats.
Real-time and early detection capabilities are critical for zero-day threats, so vendors with the latest XDR technology, behavioral analysis, and global threat intelligence are a customer’s best bet.
Read next: Best Server Monitoring Software & Tools
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.