Endpoint detection and response (EDR) is all about securing and monitoring all enterprise devices to effectively detect and respond to potential incursions. With so many servers, PCs, laptops, tablets, and smartphones accessing enterprise networks, an EDR tool is necessary to keep on top of things.
Endpoint Detection and Response (EDR) Software
What Is Endpoint Detection and Response?
Endpoint detection and response (EDR) is about collecting and analyzing data from endpoints regardless of where they are in the network — in-house, remote, or mobile. The goal is to spot and stop attacks. As well as removing threats, EDR can help to trace the source of any attacks, so that such events can be prevented in future.
In essence, EDR software provides a central hub to manage organizational endpoints. The good ones can spot and stop attacks long before a human becomes aware of them.
Read more: Best Server Security Tools
Top EDR Tools
There are a large variety of EDR solutions and services to choose from. Here are some of the best endpoint security tools, in no particular order.
Sophos
Sophos Intercept X synchronizes native endpoint security with server, firewall, and email security. It provides a holistic view of an organization’s environment with a rich data set and deep analysis for threat detection, investigation, and response. Sophos Intercept X employs a comprehensive defense-in-depth approach to endpoint protection, rather than relying on one primary security technique.
This layered approach combines modern and traditional techniques to stop a range of threats. It uses AI to detect and block malware by scrutinizing file attributes from hundreds of millions of samples, identifying endpoint threats without the need for a signature.
Key Differentiators:
- Includes anti-ransomware capabilities that detect and block the malicious encryption processes used in ransomware attacks
- Anti-exploit technology stops the exploitation techniques that attackers rely on to compromise devices, steal credentials and distribute malware
- Utilizes application lockdown, web control, data loss prevention, and signature-based malware detection
- Intercept X and Sophos Firewall will share data to automatically isolate compromised devices while cleanup is performed, then return network access when the threat is neutralized
- Employs deep learning AI to stop never-before-seen threats
Trend Micro
Trend Micro Vision One provides EDR capabilities across email, endpoints, servers, cloud workloads, and networks. It is a purpose-built threat defense platform that provides extended detection and response (XDR) capabilities to collect and automatically correlate data across multiple security layers. It prevents the majority of attacks with automated protection.
Key Differentiators:
- Uses native sensors and protection points coupled with XDR capabilities to stitch together threat activity across layers, allowing for the quick detection of complex attacks that bypass prevention
- Managed XDR service can augment teams with expert threat hunting and investigation
- Automatically ties together a series of lower-confidence activities into a higher-confidence event, surfacing fewer, prioritized alerts for action
- More context, less noise with MITRE Adversarial Tactics, Techniques and Common Knowledge (ATT&CK) mapping
- Role-based views of multiple risk metrics and trends
- Detection rules are added regularly, based on what Trend Micro threat experts are finding in the wild
CrowdStrike
CrowdStrike offers Falcon Insight as an EDR software solution. It delivers continuous endpoint visibility that spans detection, incident response, and forensics to ensure nothing is missed and potential breaches are stopped. It continuously monitors all endpoint activity and analyzes the data in real time to automatically identify threat activity, enabling it to both detect and prevent advanced threats as they happen.
Key Differentiators:
- Falcon Discover allows users to quickly identify and eliminate malicious or noncompliant activity by providing real-time visibility into the endpoint devices, users, and applications in the network
- CrowdStrike Falcon Prevent is a Next-Generation Antivirus (NGAV) service that combines prevention technologies with attack visibility and simplicity
- Uses indicators of attack (IOAs) to automatically identify attacker behavior, sending prioritized alerts to the Falcon user interface (UI)
- CrowdScore Incident Workbench provides a comprehensive view of an attack from start to finish, with deep context for faster and easier investigations
- Mapping alerts to the MITRE ATT&CK framework allows you to understand even the most complex detections at a glance, reducing the time required to triage alerts, and accelerating prioritization and remediation
Ivanti
Ivanti Neurons for Unified Endpoint Management (UEM) offers visibility into the entire asset estate, bringing in mobile devices and combining them with traditionally managed devices. It enables a higher level of automation, as well as a single source of truth for all devices.
Key Differentiators:
- User and device views cut complexity, long wait times, and high escalation costs
- Ivanti Neurons for Discovery delivers accurate asset information in minutes, automatically discovering and mapping the linkages between key assets and applications
- Provides active and passive scanning, as well as third-party connectors
- Discovery and inventory database interconnects with other data sources, such as hardware warranty information, vendor licensing rules, or reseller purchasing information
- Discover and inventory all IT assets in real time to improve security posture
Cybereason
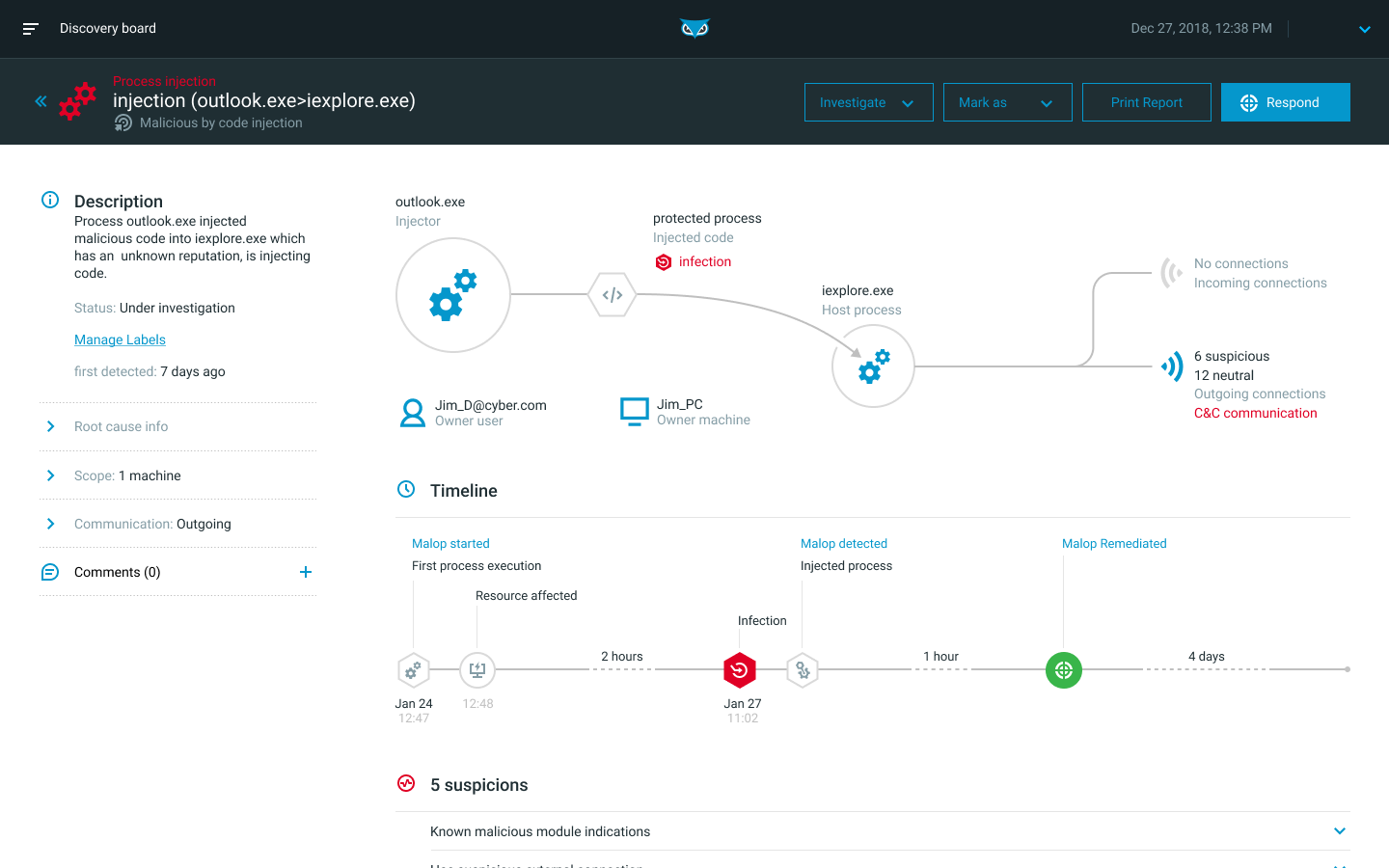
Cybereason Enterprise combines prevention and endpoint security controls with rapid detection to leverage contextual correlations across all endpoints in real time. It consolidates all intelligence about each attack into a single visual representation called a Malop (malicious operation).
Each Malop organizes the relevant attack data into an easy-to-read, interactive graphical interface, providing a complete timeline of the attack, the flow of malware across processes and users, and all incoming and outgoing communications for affected machines.
Key Differentiators:
- Remediate at scale with actions that can be automated or accomplished remotely
- Empower analysts of all skill levels to dig into the details of an attack without crafting complicated queries
- Pivot directly from investigating a Malop to remediating affected machines with machine isolation, process killing, and persistence mechanism removal
- Automated threat hunting to uncover IOCs and IOBs (indicators of compromise and behavior) hidden within the environment
- Detect malicious activities correlated across devices in real time without the need for SOC teams to spend time configuring detection rules
Netenrich
Netenrich works with small and midsize companies on right-sizing their security operations and driving their digital transformation efforts. Its XDR services enable continuous, full visibility and coverage across all network assets and hybrid cloud environments.
Key Differentiators:
- Managed detection and response (MDR) for endpoints, on-prem infrastructure, and cloud infrastructure
- Provides threat hunting, as well as fast detection, prioritization, and resolution of threats
- Offers remediation services and professional services
- Offers an AI/ML automation platform complemented with human intelligence
- Integration with other cybersecurity tools
Cynet
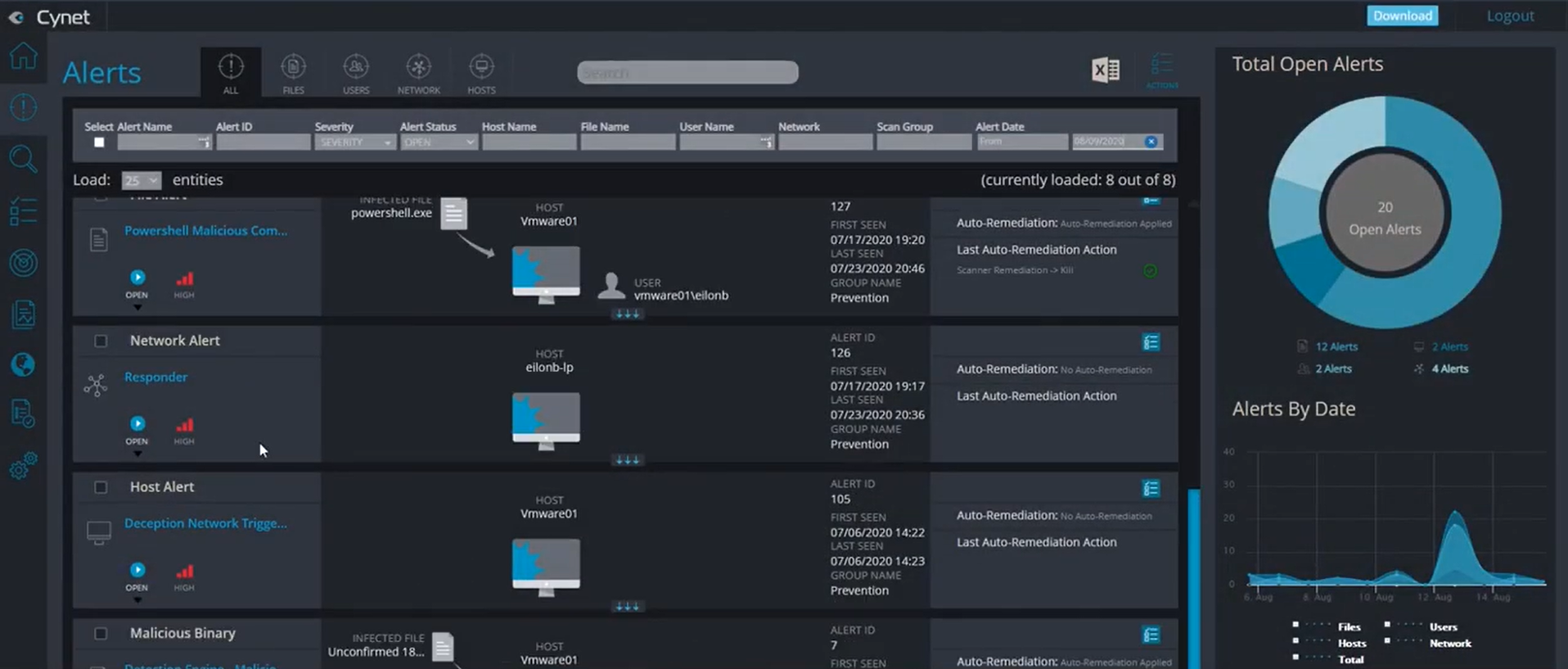
Cynet XDR prevents and detects threats on endpoints, networks, and users. For each identified threat, it triggers an automated investigation flow that reveals the attack’s scope and root cause, and applies automated remediation. It works in conjunction with CyOps, Cynet’s 24/7 SOC team of threat researchers and security analysts.
Key Differentiators:
- Cynet Prevention & Detection leverages Cynet Sensor Fusion to provide the integrated capabilities of antivirus, endpoint detection and response, network analytics, deception, and user behavioral analytics
- Cynet Response Orchestration includes a set of remediation actions to address infected hosts, malicious files, attacker-controlled network traffic, and compromised user accounts
- CyOps assist with in-depth investigation, proactive threat hunting, malware analysis, and attack reports
- Provides exclusions, whitelisting and tunneling
- Deep dive into validated attack bits and bytes to gain the full understanding of scope and impact, providing the customer with updated IoCs
- Conclusion of investigated attacks entails concrete guidance to the customers on which endpoints, files, users, and network traffic should be remediated
What Is an EDR Tool?
EDR tools vary from vendor to vendor. Most incorporate antivirus tools. Others offer a blend of functions such as machine learning, behavioral analysis, threat monitoring, detection of indicators of compromise (IoC), and ransomware protection.
A great many vendors and Managed Service Providers (MSPs) are now offering EDR. EDR is available on-premises, in the cloud, as a hybrid solution, or as a purely managed service. When fully managed, the EDR software is often called MDR. Some vendors add advanced functions, calling the service XDR.
Generally speaking, most EDR software provides a majority of these functions:
- Threat hunting: Threat hunting combats ransomware defense to find threats before they’re able to deploy ransomware.
- Threat intelligence: Threat intelligence is key to understanding threat actors and the way they operate. Security teams can gain a better understanding of specific threat actors and their most commonly used tactics, techniques, and procedures (TTPs) in order to better prepare their environments to more effectively defend against the most prominent threats.
- Threat response: The ability to take targeted actions to neutralize threats on the customer’s behalf, as opposed to simply notifying them of potential or imminent threats. An effective MDR can not only provide remediation actions when potential threats are lurking, but incident response actions when an active attacker is at work.
- Coverage: The service should be 24/7/365, with analysts who can respond any time of day or night.
- Antivirus: A lot of organizations are still relying on signature-based AV technology. Machine learning is becoming the gold standard for classifying events as good or bad, even if the algorithm has never encountered an event of its kind before.
Choosing a MDR Provider
Depending on your organization’s needs, it may be beneficial to opt for a managed detection and response service. With MDR, it is important to determine whether the technology used by the operators is included in the price of the service. Some will require you to purchase your own tools (such as EDR software) separately. Others will offer the full technology stack in addition to the services component. Ideally, an organization should be able to share its endpoint and network data with the MDR provider.
Further, MDR offerings need granular real-time endpoint visibility to catch and stop modern attackers. Above all, you need expertise from an MDR provider. How big is the service? How many attacks have they stopped? You want to be backed by a team who has the experience to not only detect an attack, but also the ability to quickly investigate and respond.



