

Windows Administrative Tools are a set of features that system administrators and advanced users can access for critical tasks. They are accessed via the control panel under the Administrative Tools folder. The folder contains icons to access each feature. The number and name of the tools might vary depending on the edition of Windows.
With Windows Admin Tools, users can monitor hardware and software behavior, schedule tasks, manage Windows services, monitor logs and events, install and maintain network protection software, track endpoint devices, defragment and optimize disks, resolve security issues, and more.
This guide will dive into the Windows Admin Tools that usuallu ship with the Windows OS, as well as additional Microsoft tools users should know about and top third-party admin tools on the market.
Windows Admin Tools is a collection of tools that help manage and troubleshoot Windows computers. They include tools for monitoring system performance, configuring security settings, managing network connections, and more.
Windows Admin Tools are useful for advanced users and system administrators who want more control over their Windows devices.
There are a few best practices to consider before using Windows Admin Tools. While they are designed to increase performance and help users make the most of the Windows operating system, some tools may require advanced knowledge.
Before using a tool, make sure you have administrative privileges. Additionally, remember that some tools are more advanced than others. Do proper research for each tool before using it and only modify settings if you know exactly what you are doing.
Component Services enables the configuration and management of Component Object Model (COM) and COM+ applications. It can be used to create, deploy, and configure COM and COM+ applications and their components.
COM and COM+ protocols are critical for the operation of a wide range of software, from the Microsoft Office suite of productivity applications, to specialized design software like Adobe Photoshop or AutoCAD.
COM mechanisms and COM+ protocols also allow applications to communicate with other applications, ensure interoperability, enable plug-ins and automation, and manage transactions, synchronization, and multiple object class configurations. They also enforce security and provide additional features.
To implement this Windows administrative tool, user systems must be appropriately configured. Administrators are then free to make initial adjustments to COM applications and services, and install COM+ applications. Administrators can monitor and tune Component Services applications to optimize performance, security, and more.
Computer Management is a set of Windows admin tools that you can use to control a local or remote computer. The tools are grouped into a single console, making it convenient to see administrative properties and access the tools required to perform computer management tasks.
The Computer Management console is divided into two panes. The left pane contains the console tree and the right pane includes details. When you click an item in the console tree, information about that item is displayed in the details pane.
Tools in Computer Management are grouped into the following categories:
Administrators can access Computer Management features on a local or remote computer. For local computers, users can open “Computer Management (Local),” where the console tree and tool categories are available for admin visibility.
Administrators must select “Another Computer” on remote computers to manually add or locate the target computer. Similarly, admin users can view the tools and services for the remote device.
The Task Scheduler allows users to create, modify, and disable computer tasks that run at specific times or in response to certain conditions being met. For more intensive processes, task scheduling can be critical to allocating CPU without causing degradation of other computer systems.
To use Task Scheduler, administrators can access the tool via the Windows Administrative Tools folder or via the command prompt “taskschd.msc”.
The Task Scheduler Library gives admin users visibility into the root folder containing all tasks.
Details like trigger conditions are events prompting a specific job. The execution of this task is known as the action and can include defragging, sending an email, running an app, and more.
Event Viewer is a tool that keeps track of events in the system. It records logs about programs, security, and system events.
Log management is essential for administrators that need visibility into specific components, services, and user traffic. You can use Event Viewer to see and manage the event logs, find information about hardware and software issues, and monitor Windows security events.
Administrators can access the Event Viewer to select from particular logs. After choosing a log, the admin can filter, sort, and search event data and evaluate available binary data. Event Viewer records are available as EVT log files when saved, and as TXT and CSV files when archived.
Users running Windows OS on computers or servers can use the Performance Monitor to understand how features, apps, and devices work. The tool can also generate reports and graphs and help troubleshoot why something is slow or broken.
The Performance Monitor has always been a simple but powerful visualization tool, but with Windows 11, its design and interface have been upgraded and modernized (Figure D).
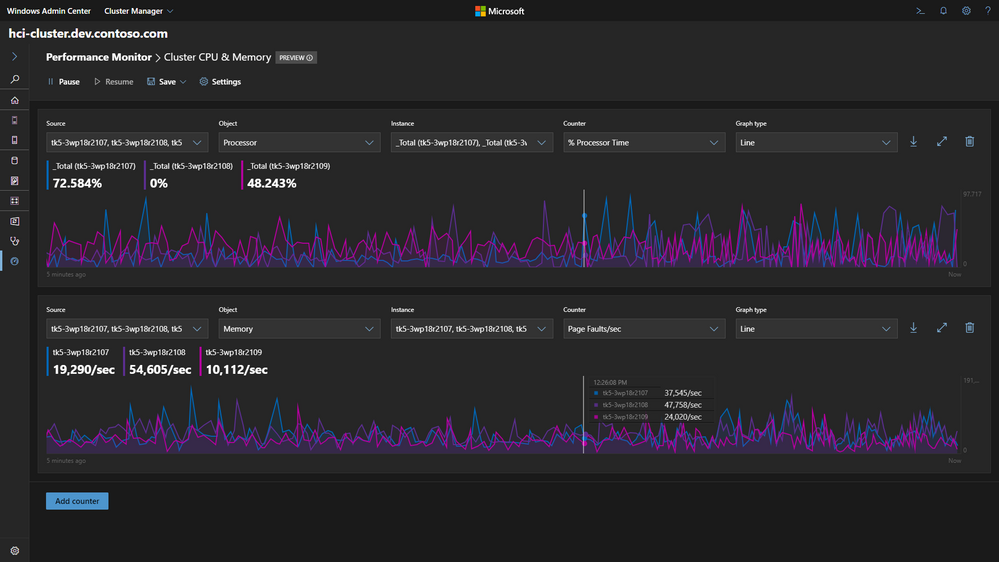
With Performance Monitor, users examine performance data in a graph, histogram, or report and modify settings. This tool uses event trace data, configuration information and performance counters to evaluate how services and applications affect computer performance.
Depending on the administrator privilege group, users can view performance and reliability monitors, use Resource View, modify Data Collector Sets, or change the monitor display properties.
Admin users can also use Performance Monitor to view real-time performance data on a remote computer by selecting Reliability and Performance from the monitor console to connect another computer by name or local network.
Defragment and Optimize Drives in Windows reorganizes fragmented data so disks and drives can operate more effectively.
Fragmentation is what happens when a computer’s files scatter across disk drives, eventually causing performance degradation and reducing computing speed. To solve these issues, users can turn to the Defragment and Optimize Drives tool.
Drive optimization happens automatically on a regular basis, but you can also check and defragment disks and storage drives manually if you want to get ahead of any performance issues.
To use the tool, follow these steps:
Depending on the computer’s hardware and software and the size of the disk, the tool might take anywhere from several minutes to a few hours to finish defragmenting.
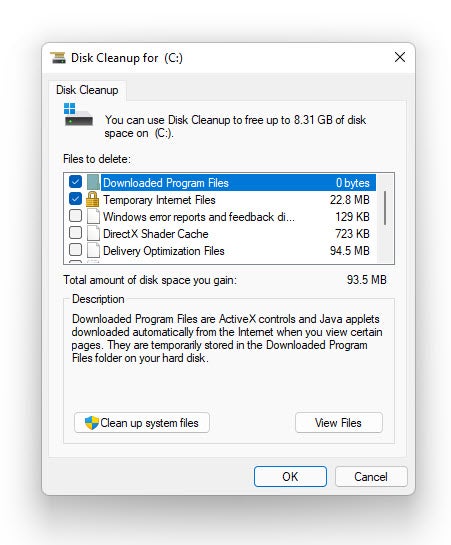
Disk Cleanup is a software tool that helps users free up disk space. Disk Cleanup can help computers run faster and more efficiently by removing unnecessary clutter from hard drives, such as temporary files, cached web pages, and items in the Recycle Bin. You can also delete system files with Disk Cleanup if you need to free up additional space.
To use Disk Cleanup:
Services is a Microsoft Management Console (MMC) snap-in responsible for running background services. Without a GUI for end users, the Services snap-in is similar to a daemon process in UNIX systems. These background processes are central to operating system functionality, including event logging, file serving, error reporting, web serving, and cryptography.
To access the tool, press the Windows + R keys to open the Run window. Type “services. msc” and hit Enter, or click the OK button.
When launched, Services offers various configuration options for managing computer services. Admin users can adjust services in real time, establish service redundancy, configure hardware by services, and view service dependencies.
Services data is exportable as a TXT or CSV file for sharing and preserving the status and description of services as a reference point.
The Internet Small Computer Systems Interface, known as iSCSI, is an IP standard for connecting to network storage devices. Administrators use the Microsoft Internet iSCSI Initiator to connect computers to external iSCSI-based storage devices and iSCSI storage area networks (SAN) by ethernet network adapter.
SANs provide iSCSI target functionality without investing in additional hardware, enabling iSCSI storage devices in homes and small offices.
Administrators can transmit iSCSI data over local area networks (LANs), wide area networks (WANs), or the internet.
Administrators can access the Microsoft iSCSI Initiator GUI to quickly discover and establish connections to storage devices, or create a configuration report detailing all links. For implementation, the iSCSI Initiator comes with functionality for data digests, multipath I/O (MPIO), IPv6 compatibility, Internet Protocol security (IPsec), CHAP, remote boot, and naming service (iSNS).
Once fully installed, the Microsoft iSCSI Initiator comes with a unique iSCSI qualified name (IQN) based on the computer name and DNS. Administrators can configure initiators to always reestablish connections upon device reboots, automatically start services on iSCSI disk volumes, and generate iSCSI configuration reports.
The iSCSI Initiator sends SCSI commands to the iSCSI target device, which then performs the requested operations and returns the results. The iSCSI Initiator also makes the iSCSI storage device appear as a locally attached disk, which can be used for various purposes such as running enterprise applications or storing data.
Local Security Policy is the control console for the individual device’s security policies. Security policies related to passwords, lockouts, audits, access and more are all available for administrators to provision. Other security setting options include configuring Windows Defender Firewall, public key policies, application control policies, and IPsec.
Organizations with Microsoft infrastructure rely on Active Directory to set group security policies. Still, administrators can also view and configure a single device’s settings with access to the Local Security Policy. Unlike domain security settings, this tool provides insight into the security policies of a standalone device.
To view and edit a local security policy:
Short for Open Database Connectivity, ODBC Data Source Administrator is a tool for managing database drivers and data sources. Drivers process ODBC traffic and adjust requests to meet protocol, while data sources are the files and databases accessed by drivers.
The types of data sources include those limited to a specific user, all users on a single device, or shared files through a network database.
This tool provides interoperability when an application needs access to multiple data sources. Using SQL queries, administrators can establish application access to data sources and specific database management systems (DBMS).
Print Management allows administrators to connect, centralize, and manage print servers and network printers. Print management functionality includes three core services:
Print Management is available for local or remote configuration. It can be used to set up printer connections for multiple client computers at once and to check print queues from a distance.
The tool can also help users locate printers with problems by using filters, and even send email alerts or run scripts when a printer or print server requires attention.
The LPD service enables the TCP/IP Print Server to connect other remote printers, but stopping or restarting the print spooler service requires administrators to restart these services manually.
For a full tutorial on how to use this multifaceted tool, you can browse Microsoft’s official Print Management support page.
The Windows Resource Monitor is a vital tool for monitoring resource usage and evaluating problems related to resource traffic. Split into five tabs, the Resource Monitor includes CPU, memory, disk, network views, and filter options to analyze specific processes and services. All monitor tabs contain multiple tables.
Admin users can access the Resource Monitor via resmon.exe or the Windows Administrative Tools folder. Administrators can navigate between tabs that contain multiple tables offering standard search and filter functions.
Each tab also includes a chart pane with graphical views of resource usage. Administrators can customize viewing options between the tabs, tables, and chart panes to optimize visibility.
System Configuration allows administrators to alter how the Windows operating system boots.
Administrators can use System Configuration for routine, diagnostic, and selective startup options. This tool allows admin users to manage startup programs and tracks entry alterations for optimizing system starts.
System Information offers a plethora of data about hardware resources, components, software environments, and Microsoft Edge to enhance administrator visibility into problems and offer remediation steps.
Hardware resources include settings like I/O addresses, memory addresses, interrupt requests (IRQs), and direct memory access (DMA). The Components feature shows the status of connected devices, ports and USB drives, while the Software Environment offers a snapshot of drivers, running tasks, services residing in computer memory, and more.
Administrators often need System Information for visibility into the various hybrid systems in modern IT environments.
With more profound insight into specific process issues, admin users can take action with tools like disk cleanup, backups, diagnostics, file signature verification, and a hardware wizard.
The Windows Report Tool collects this data for admin use and continued evaluation.
Windows Firewall with Advanced Security is designed to secure devices on your network. The tool includes a stateful firewall that lets users decide which network traffic can pass between their computer and the network. It also provides connection security rules that use IPsec to protect traffic as it moves across the network.
Administrators can manage firewall rules dictating allowed and blocked traffic and connection security rules which secure traffic between the host and other computers. Both rule types combine to offer individual devices foundational intrusion prevention capabilities.
The Windows Firewall and Advanced Security MMC snap-in combine firewall and IPsec settings in a single GUI where administrators can set reasonable traffic policies. The IP Security Monitor specifically offers statistics for how policies impact activities.
With Netsh, administrators can also access a command-line tool to configure network component settings. This tool enables the creation of scripts for configuring Windows Firewall and IPsec and displaying the status of both devices.
Windows Memory Diagnostic is a tool that can run a wide range of tests on system RAM to determine any problems with any modules. It is used when a computer is freezing, crashing, or its performance has been slowed, to identify and later fix the problem.
To run the Windows Memory Diagnostic, press the Windows + R keys together to access the Run utility. Type “mtsint.exe” and hit Enter in the search bar.
The tool offers administrators two options: create a startup disk, or save a bootable CD image to the computer’s hard drive.
The tool can run six memory tests using unique algorithms, scan for different error types, and alert the administrator to memory addresses and errors as discovered. The Extended mode includes 11 separate memory tests. In either case, admin users can evaluate successful and failed tests for faulty RAM modules and underlying errors.
In addition to the preinstalled tools discussed above, there are some freely available Windows admin tools that are available from Microsoft. Here are some of the best ones you should know about.
Remote Server Administration Tools (RSAT) allow IT administrators to remotely manage roles and features on Windows Servers. This tool can also remotely manage Windows Active Directory for domain-level policies. RSAT has become an even more valuable tool, given the recent boom in remote work ecosystems.
With RSAT, there’s no need for a remote desktop protocol (RDP), which can be time-consuming to implement, maintain, and secure consistently. The RSAT package includes command-line tools, Windows PowerShell cmdlets, Hyper-V, the MMC snap-in, and a server manager.
The Windows Best Practices Analyzer (BPA) is a natively integrated Windows Server tool. It ensures that Active Directory (AD) follows Microsoft’s best practices standards by analyzing key settings and other AD components.
The BPA can help administrators identify ways to increase the security and performance of AD. Each setting or component scanned displays status and description for admin user visibility. The BPA is also compatible with monitoring the health of Hyper-V.

The Microsoft Windows PowerShell ISE is a GUI-based application and interactive environment built on the .NET Framework. It is the default editor for Windows PowerShell commands and allows System Admins to run various PowerShell commands in real time. PowerShell ISE can automate several administrative responsibilities related to managing applications running on a network.
There are also Script Browser and Script Analyzer add-ons available for PowerShell ISE. The Script Browser automatically searches for and identifies appropriate command scripts for specific tasks using the TechNet database. Administrators can save time and effort manually searching through libraries of scripts while the Script Analyzer evaluates and suggests changes to improve script effectiveness.
Aside from all of Microsoft’s native administrative apps, there are some handy third-party admin tools that provide additional functionality. Here are a few of our favorites.

Best free network monitoring tool
Wireshark is the most used network protocol analyzer available. This free and open-source networking monitoring tool is excellent for diagnosing network issues and guiding administrators toward the appropriate remediation.
While Wireshark is great for Windows systems, it also has cross-platform compatibility supporting macOS, Linux, Solaris, FreeBSD, NetBSD, and OpenBSD.
Wireshark offers a clear and logical GUI based on the popular toolkit GTK, with a standard three-pane packet browser. Valuable features include live capture, a rich VoIP analysis, and deep inspection of hundreds of protocols.
Capture files are compressible with gzip, and administrators can export data via TXT, CSV, PostScript, or XML.

Best free backup and disaster recovery tool
Clonezilla is a free tool for cloning disks and individual hard disk partitions. It can prevent the permanent loss of precious data and help organizations prepare for when disaster strikes.
Clonezilla is a fast and reliable tool for single machines (Clonezilla Live) and large deployments (Clonezilla Lite Server and Clonezilla Server Edition).
Clonezilla SE can install an operating system and software applications on one machine, then take a snapshot and deploy it on other network devices. This version can also backup other machines connected to the network.
Clonezilla supports a wide variety of file systems, including FAT, NTFS (Microsoft), extended file systems (Linux), Reiser4, and VMFS (VMware).

Best suite of free server administration tools
ManageEngine Desktop Central is a suite of free Windows administrative tools for managing endpoints from a central space. It’s not open-source or a native Windows tool, but its free edition is suitable for SMBs managing up to 25 computers or mobile devices.
ManageEngine’s Windows Server administrative suite includes various Windows administration and management tools, such as remote control, patching, software inventory, rebooting, disk monitoring, asset management, and more.
With Desktop Central’s remote functionality, administrators can troubleshoot issues on individual machines from any location.
Windows Administrative Tools are powerful resources designed to enhance performance. However, it is essential to know what each tool is, how it works, and how to use it to leverage the technology safely and effectively.
Armed with a strong understanding of the variety of uses of these tools, system and server admins can successfully manage security, performance, connectivity, interoperability, and more.
Go deeper on server management with our guide to the best free RADIUS testing and monitoring tools.


Ray is a Content and Communications Specialist with more than 15 years of experience. He currently works at Publicize and as a contributing writer for TechRepublic, eSecurityPlanet, and Enterprise Networking Planet in addition to ServerWatch. His work has also been published in Microsoft, Venture Beat, Forbes, Entrepreneur, The Sunday Mail, FinTech Times, Spiceworks, Dice Insights, Horasis, the Nature Conservancy, and other leading publications.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.