

As virtualization becomes the norm for organizations around the world, securing these environments where business-critical operations run is vital. From zero-day exploits to denial-of-service (DoS) attacks to hyperjacking, the threats to virtualized architectures are extensive and potentially damaging.
Organizations need to include security from the early stages of virtualization projects, understand the vulnerabilities of virtual machines and hypervisors, and implement best practices to increase their privacy, governance, and cybersecurity postures.
This article will give you five simple steps organizations can take to secure their virtualized data centers.
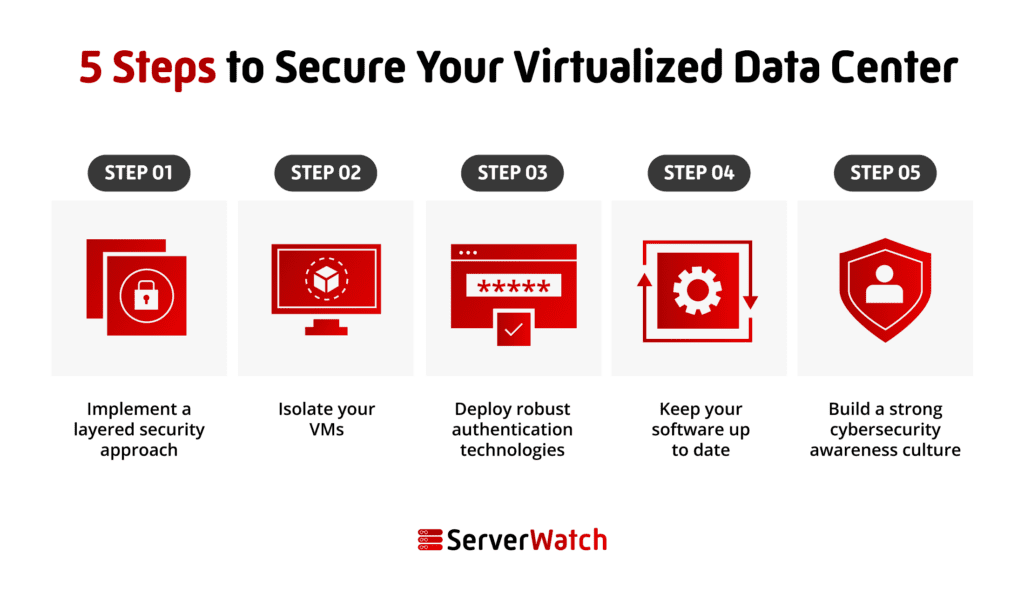
Now, let’s look at how organizations can take control and ownership of virtualized cybersecurity and mitigate threats and risks with five simple steps.
Companies must implement a layered security approach, combining different security controls to protect VMs, hypervisors, networks, and the underlying infrastructure. Layered security solutions include firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), anti-malware, network security, authentication technologies, and more.
Here are some specific examples of layered security controls that you can implement:
Most virtualization vendors offer layered security solutions for their environments. Companies should identify their highest-value assets, and weaknesses and talk to their vendors to find the right solutions to secure them. A proper configuration is also essential to prevent exposure and mitigate risks.
Some forms of virtualization, such as full virtualization, offer a higher isolation level than other types, such as paravirtualization — where a VM collaborates with the hypervisor and may share resources with other VMs. However, no matter which type of virtualization a company chooses to deploy, isolation degrees are important.
There are many ways to isolate VMs from each other. Companies can create fully isolated VMs, or use VLANs, network segmentation, and other technologies. Isolation will help prevent attackers from being able to move laterally between VMs if they are able to compromise one VM.
There are also ways to limit the communication between shared resources, allowing only those protocols that are necessary for the operation to run. Limiting the communication between resources prevents security breaches in the data center and in some cases might even be required by law.
Authentication access technologies help companies visualize and understand who is connecting to a VM, from what device, and whether they are authorized and verified. A zero trust approach, where every connection and every user is considered and treated as malicious until authenticated and verified, offers the highest level of protection.
Companies should also implement strong passwords and mandatory MFA policies, use least privilege access, giving users only the access they need to perform their jobs, and use role-based access control (RBAC) to assign users to roles that have specific permissions.
Monitoring and profiling users and devices can also help detect suspicious behavior and support security incident response efforts as well.
Cybercriminals are constantly finding new ways to breach systems. Keeping software up to date is the best way to make sure all new security patches relevant to your virtualization software, guest operating systems, and other applications are being applied. Additionally, many cybersecurity solutions require updates to be effective against new malware variants.
To keep software up to date, companies can:
Companies must create a robust cybersecurity awareness culture within their entire organization. Workers need to be informed, educated, and skilled about best practices and real techniques used by cybercriminals. It is also important to run real phishing simulations to detect the weakest point of entry.
As mentioned above, most attacks happen due to human error or sophisticated social engineering techniques. Companies that have hundreds of workers are at a higher risk. All it takes for an attacker to breach a system is to find that one employee that will click on the wrong link, visit a website they shouldn’t, or open an attachment that contains malware.
From password security to how to identify scams and common security pitfalls such as misconfiguration threats, an awareness program must make sure to cover it all. We also encourage rewarding and recognizing employees and identifying cybersecurity leaders at your organization. To keep a company up to date, managers can also send out regular send out security newsletters and reminders to employees.
Before beginning to implement virtualization security technologies, companies must understand the specific threats that affect these systems.
Hypervisors are the software that manage and orchestrate virtual machines (VMs). Vulnerabilities in hypervisors or VMs can give attackers access to all VMs on a host server.
Hypervisor and VM vulnerabilities include:
Within these vulnerabilities the level of isolation each VM has is vital. For example, in side-channel attacks, criminals exploit vulnerabilities in hardware or software to steal data from VMs. An attacker could use a side-channel attack to steal encryption keys from a VM that is running a database.
Virtualized environments may also be affected by accidental, illegal, or unauthorized disclosure of sensitive data and data leakage. This can happen when VMs are not properly configured or when data is not properly encrypted.
In contrast, DoS attacks can be used to overwhelm VMs and make them unavailable to users. This can be achieved simply by flooding a VM with traffic or by exploiting vulnerabilities in the VM’s operating system.
Finally, malware such as ransomware, spyware, trojans, or stealware can breach VMs and steal data, disrupt operations, or even take control of the entire environment. Often cybercriminals deploying these types of malware attacks use phishing and social engineering as their preferred vector to breach a system.
The specific technical software and hardware security solutions that a company will need to deploy to secure its virtualized data centers will vary on a case-by-case basis. However, while each environment may have specific demands, they all share common ground.
By creating a layered cybersecurity infrastructure, ensuring authentication technologies and policies are in place, isolating VMs, properly configuring systems and networks, and continually monitoring the environment, companies can stay one step ahead of attackers, and strengthen their governance and privacy.
In the event of data loss or theft, make sure you are relying on one of the best VM backup companies to recover and restore your critical data.


Ray is a Content and Communications Specialist with more than 15 years of experience. He currently works at Publicize and as a contributing writer for TechRepublic, eSecurityPlanet, and Enterprise Networking Planet in addition to ServerWatch. His work has also been published in Microsoft, Venture Beat, Forbes, Entrepreneur, The Sunday Mail, FinTech Times, Spiceworks, Dice Insights, Horasis, the Nature Conservancy, and other leading publications.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.