

A Network Policy Server (NPS) allows network administrators to create and enforce policies for network access, ensuring that only authorized users and devices can access network resources. This versatile tool plays a key role in centralized authentication, authorization, and accounting for users and devices that connect to a network.
Essentially, NPS is Microsoft’s implementation of a Remote Authentication Dial-In User Service (RADIUS) server and proxy in the Windows Server operating systems. It is a crucial component in network management and security.
To better understand NPS, we’ll first take a look at what RADIUS servers are, then explore the purpose of NPS, its benefits, its role in networking, and best practices for managing an NPS.
With the increasing reliance on technology and the internet for business operations, data exchange, and communication, networks and servers have become primary targets for cyberthreats. This elevated risk landscape underscores the necessity of robust network security and meticulous policy management.
Here are the key reasons why network security and policy management are important:
The RADIUS protocol is a networking protocol that provides comprehensive and centralized Authentication, Authorization, and Accounting (AAA) management for users who connect and use a network service.
Since its inception in 1991, RADIUS has become a standard for network access servers responsible for connecting users to networks, playing a pivotal role in managing network access control.
The first A in AAA refers to Authentication, or the process of verifying a user’s identity. When a user attempts to access a network, they must provide credentials, such as a username and password.
The RADIUS server checks these credentials against its database to confirm the user’s identity. This process ensures that only legitimate users can access the network.
Once a user is authenticated, the next step is Authorization. This process determines what an authenticated user is permitted to do on the network.
For example, an administrator may have different access rights compared to a standard user. RADIUS servers manage these permissions, ensuring users can only access resources appropriate to their authorization level.
The final A stands for Accounting, which involves tracking the usage of network resources by users. This includes monitoring the amount of time users are connected, the services they access, and the data they transfer. This information is crucial for billing, auditing, and understanding network usage patterns.
RADIUS operates in a client-server model. The RADIUS client, usually a network access server like a VPN or wireless access point, sends user credentials and connection requests to the RADIUS server.
The server then processes these requests against its user database and policies to authenticate and authorize the user. Post-authentication, it sends a response back to the client, either granting or denying access.
Some of the main features of RADIUS servers are:
An NPS serves as a critical element within the network infrastructure of many organizations, primarily functioning as Microsoft’s implementation of a RADIUS server and proxy. The overarching purpose of NPS is to centralize and streamline the authentication, authorization, and accounting (AAA) of users and devices accessing a network, thereby enhancing security and management efficiency.
Centralized authentication ensures that all users and devices are verified before gaining access to network resources, enhancing security. Authorization, on the other hand, defines what resources authenticated entities are permitted to use.
Below are how an NPS server manages these crucial functions to maintain a secure and efficient network environment.
Accounting involves tracking and logging user activities and resource usage within the network, which is pivotal for auditing and monitoring purposes. The following list discusses how NPS aids in ensuring compliance with various regulatory standards, a critical factor for businesses in today’s data-sensitive world.
Policy-based network management allows administrators to create and enforce specific network access policies, tailoring network security and usage according to organizational needs. Here is how NPS facilitates the creation of these policies and how they impact network security, user access, and overall network management:
The implementation of NPS in a network infrastructure offers a range of benefits that enhance both security and operational efficiency. These advantages make NPS a valuable asset for organizations looking to optimize their network management practices.
NPS fulfills three key roles in managing network access and policies. Each role represents a distinct functionality that contributes to the comprehensive network management capabilities of NPS.
NPS processes authentication and authorization requests for network access. When a user or device attempts to connect to the network, NPS verifies their credentials and determines their access level based on predefined policies.
Additionally, NPS can work with a variety of network access servers, such as VPN servers, wireless access points, and dial-up servers, making it a versatile solution for different network types. It is also pivotal in enhancing network security by centralizing and streamlining the authentication process, thus efficiently managing user access across the network.
When functioning as a RADIUS proxy, NPS forwards authentication and configuration requests to other RADIUS servers in the network. This is particularly useful in complex or distributed network environments. Also, it can provide load balancing by distributing requests among multiple RADIUS servers and ensure continuity through failover mechanisms in case of server unavailability.
This role enables NPS to handle requests across different networks or sub-networks, facilitating seamless cross-network authentication and management.
NPS primarily manages and enforces network policies. It defines the conditions under which users and devices are granted or denied network access. It also allows the creation of policies based on various conditions like time of day, group membership, or the health status of a device, providing a high degree of control over network access.
In this role, NPS can also integrate with NAP to enforce device health policies, ensuring that only compliant and healthy devices can access or communicate on the network.
Using NPS effectively requires adherence to certain network and server management best practices. These practices ensure that NPS operates efficiently, securely, and in alignment with the organization’s network management goals. Here are some recommendations from Microsoft:
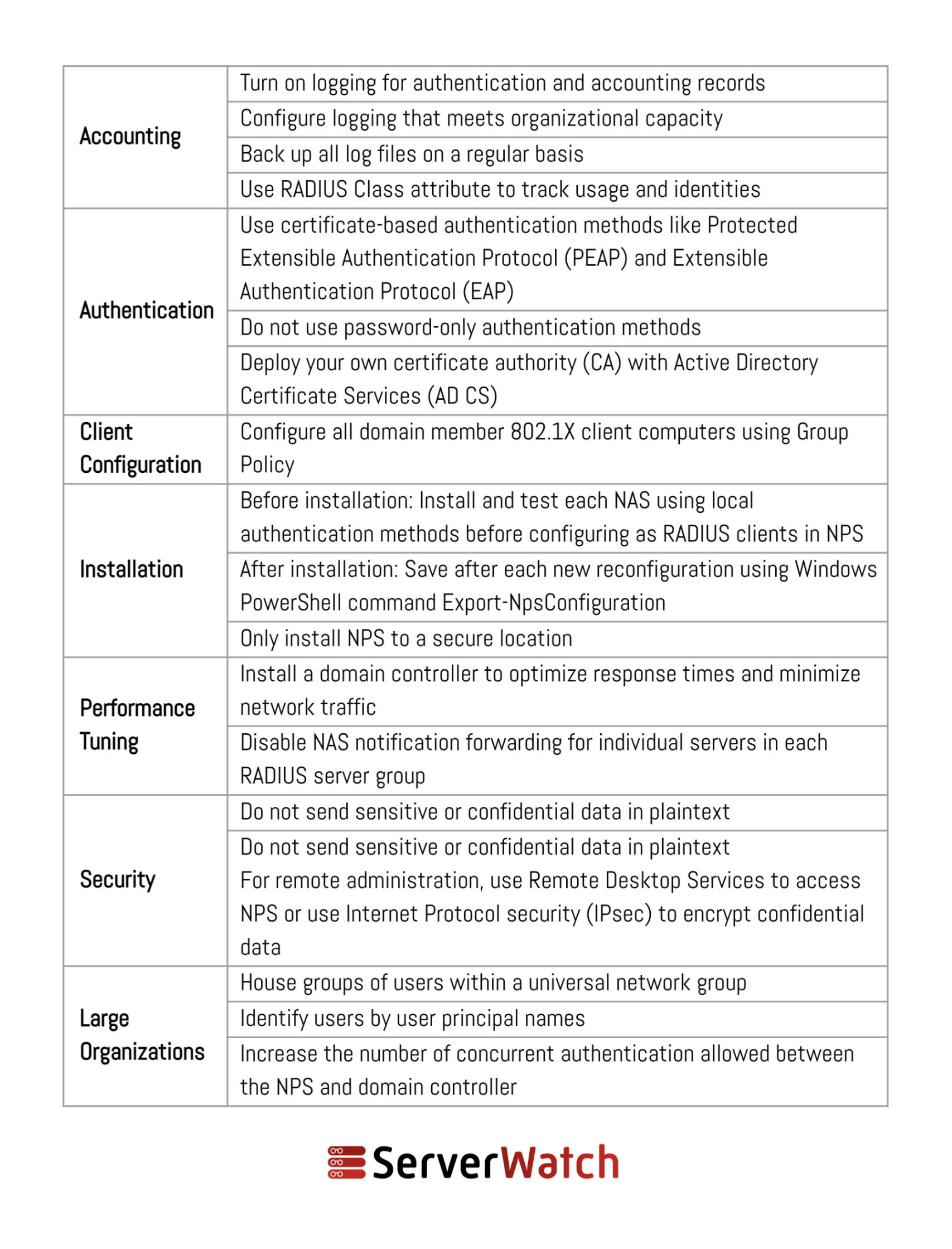
Below are some additional best practices to consider when deploying and managing an NPS.
NPS has emerged as an indispensable network and server tool offering a robust and flexible solution for ensuring secure and efficient network operations. The integration of NPS within an organization’s network infrastructure not only enhances security by enforcing rigorous access policies but also simplifies administrative tasks, leading to a more efficient management of network resources.
By adhering to best practices in deploying and managing NPS, organizations can significantly mitigate risks associated with network security and ensure a seamless operational flow.
Improve your NPS functionality and performance with one of the best free RADIUS server testing and monitoring tools, selected and reviewed by our experts.
Sam Ingalls contributed to this article.


Allan is based in Quezon City, Philippines, with over a decade of experience in the ever-evolving IT landscape. With a degree in Computer Science and another in Information Science plus eight years freelancing for B2B and tech enterprises, Allan is proud to marry first-hand skills with research-based storytelling to make the most complex topics understandable and accessible. When not navigating the realms of servers, SaaS, networking, web development, and other digital technologies, he finds solace in the imaginative worlds crafted by authors like Robert Jordan and J.R.R. Tolkien.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.