

Managing Domain Users and Groups
Local users and groups exist only in the SAM of a local Windows 2000 system, and can only be used for access on the system on which they exist. As such, local accounts are not practical for use in a large environment, due to their distributed administrative nature. As such, most companies have a domain, which of course centralizes user and group administration, as well as the authentication function, on Windows 2000 Servers acting as domain controllers. Domain controllers do not have a local SAM, but instead share and replicate the Active Directory database, where user and group objects (amongst other things) exist. In this section we’ll take a look at a number of features of accounts that still exist, but some that are different than in NT 4.
First of all, every account in Active Directory is an object, and objects can have properties. Examples of properties include things like a first name, last name, password, phone number, and so forth. There are many more properties associated with a domain user account than a local user account, as shown below (local account properties on left, domain on right):
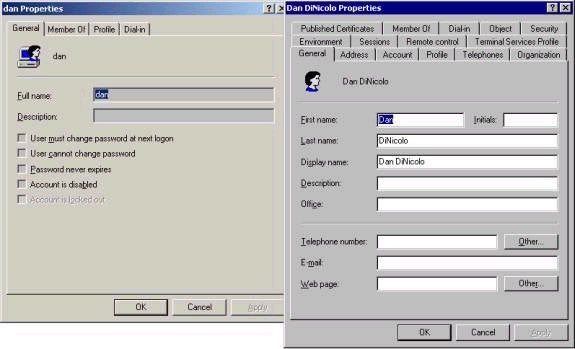
In very basic terms, local accounts are still very much like accounts in NT 4, while Windows 2000 domain accounts potentially have many more properties associated with them. Domain accounts (users, groups, computers, etc) are set up using the Active Directory Users and Computers tool.
Some basic things you should know about user and group accounts in a domain environment in Windows 2000:
– User accounts and security group accounts still have a SID (security identifier) associated with them. Renaming an account retains the SID, and may be a good idea if one person is the company replaces another, for the purpose of resource access.
– If you delete a user account, you also delete the associated SID. Creating another account with the same name will produce a new SID, and therefore an entirely new account.
– If a person is going on a leave of absence, you can still disable an account.
– The domain administrator and guest accounts cannot be deleted, but can (and probably should) be renamed. The Guest account is disabled by default.
– You can still copy user domain user accounts, as in NT 4. Note that only generic items will be copied, such as group membership and so forth. More specific properties, such as a user’s home address, will not be copied. Copying account is most useful if you create a template account for different types of users. (Note that if you create a template account and disable it, all accounts copied from this template will also be disabled until you specifically enable them). Note also that if you copy an account called Mike, for example, and the copy is called Bob, access permissions to resources associated directly to the Mike account are NOT copied to Bob.
– When dealing with group accounts, you can easily find out what other groups this group is a part of by checking the Member Of property tab. The Members tab shows other users and groups who are part of this group.
Note that Windows 2000 supports three different types of groups: Domain Local, Global, and Universal. Groups can also be nested in Windows 2000, meaning a group can be part of another group (potentially – there are rules). Note that group nesting and Universal groups are only supported in Native mode (a mode where all domain controllers are running Windows 2000), and not in Mixed mode (where you might still have NT 4.0 BDCs present). This will be covered in greater detail later in the series.
Property of TechnologyAdvice. © 2026 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.