

Of course,
after user accounts have been created, a number of common
management tasks may need to be performed. Note that while many of
these involve setting up information relating to a particular user
(phone numbers, addresses, etc), some have father-reaching
implications in terms of security. Note that the most important
account settings are found on the Account tab in the properties of
a user account. It is from here that you can require that a user
change their password at next logon, disable an account, set logon
hour restrictions, account expiry, account lockout, and so forth.
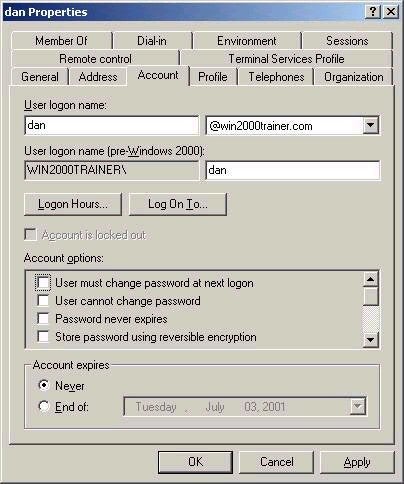
Note that
passwords are reset in Windows 2000 by right clicking on an
account and choosing the Reset Password option. In big
environments (especially ones with many OUs) you may have trouble
remembering where you created an account. To quickly find the user
(or other objects), right click the domain name and choose Find in
Active Directory Users and Computers.
A couple of additional notes on user accounts:
– Remember that an account can be renamed, without affecting the
resources that the account has access to. As such, if Bob quits
and Mark replaces him, simply rename the Bob’s account (and
change the personal information obviously) and Mary will be a have
access to everything that Bob previously did.
– Deleting an account is a big deal. When you delete an account,
the SID associated with the account is also deleted. As such, if
you were to recreate an account with the same username, it would
not have access to whatever the original account has been granted
access to, since the SID would be different. Note that a deleted
account can be restored using an authoritative restore (discussed
later in the series).
Active Directory Group Concepts
Windows 2000 Active Directory presents a number of different group
options not found in the NT domain environment. The two biggest
changes are the different types/scopes of groups that now exist,
as well as the ability to nest groups. Group accounts for domain
users are again created in Active Directory Users and Computers
First, understand that there are two types of groups: security and
distribution. Distribution groups exist for the purpose of sending
email, and do not have a SID. Security groups do have a SID, and
as such can be used to assign permissions and rights via access
control lists and policy settings.
Secondly, there are three scopes of groups: domain local, global,
and universal. A quick overview of each:
Domain Local groups: domain local groups are similar to
local groups in NT 4, except that they can be applied to any
system within a domain, not just on the system where the group
exists (since domain local groups actually reside in the AD
database). These groups are usually used to assign permissions to
resources.
Global groups: global groups are very similar to those
found in an NT 4 domain. They are still collections of users with
common needs.
Universal groups: universal groups are totally new in
Windows 2000. A universal group can contain users from any domain
in an AD forest. Similar to global groups, they are used as
collections of users with common needs or characteristics. Only an
member of the Enterprise Admins group can create a universal
group.
The screen shot below shows the dialog box you are presented with
when creating a new group:
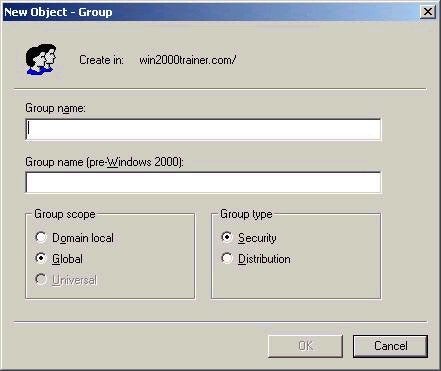
Note that the
option to create a Universal group is not available. This is
because my domain is still in Mixed Mode. Universal groups can
only be created in Native Mode. The ability to nest groups is also
new to Windows 2000, and is also only available in Native Mode.
Nesting refers to the ability to place a group into a group of the
same type – for example placing a global group into a global
group. The table below outlines group membership rules for domains
in Native Mode.
| Group Scope | May Contain |
| Domain Local | Users from any domain, global groups from any domain, universal groups, domain local groups from the same domain. Can only be used to access resources in the same domain. |
| Global | Users from same domain, global groups from same domain. Can be used to access resources in any domain. |
| Universal | Users from any domain, global groups from any domain, universal groups. Can be used to access resources in any domain. |
Active
Directory Group Strategies
Some of you will remember the group usage strategy outlined by
Microsoft for NT 4 domain environments. It suggested that you
place user accounts into global groups according to needs, assign
permissions to local groups, and then place global groups into
local groups, thereby giving users access to resources. This model
was often referred to as AGLP:
Accounts (get placed into) Global Groups (which are then placed
in) Local Groups (who are ultimately assigned) Permissions
Although there are many different possibilities in terms of
assigning permissions, the above method is amongst the most
scalable. By the same token, a methodology exists in Windows 2000
that you should follow (especially on the exam!).
Accounts > Global Groups > Domain Local Groups >
Permissions
Note that the model can extend beyond this, however. For example,
you can nest global groups (which is useful if you have a few
global groups in the same domain who you wish to further
organize), or place global groups from different domains into a
Universal group. With a Universal group, this would then make the
model:
Accounts > Global Groups > Universal > Domain Local
Groups > Permissions
The idea is simple – group users with common needs using global
groups (or universal if you wish), and then place that group into
a domain local group, which is assigned permissions to a resource.
This allows many users to have access to the resource, while
assigning permissions only once. A name for the new model that you
won’t forget? Try AGULP (just remember that the L is for
domain local now)
Property of TechnologyAdvice. © 2026 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.