Last month, we reviewed a RADIUS server targeted toward the SMB market for its 802.1X authentication capabilities, for aid in securing wireless networks with WPA/WPA2-Enterprise encryption. Now we have reviewed another server, ClearBox Enterprise RADIUS Server 2.3 from XPerience Technologies. This solution caught our eye due to its low price point and seemingly high feature set. Its web site gives the impression that it is an advanced, carrier-class, server also appropriate for the less-experienced, while being one of the lowest priced solutions for WLAN authentication. We set out to put it through the ropes to see if it did indeed offer such as remarkable solution.
General Server Features
|
Other Articles by Eric Geier
» A RADIUS Server That Comes ‘Round for SMBs » Server Room DIY, Installing Apache and Configuring Your Network » Server Room DIY, In-House Web Server Requirements Read More Reviews |
No matter how much experience you have with RADIUS servers, XPerience Technologies’ ClearBox’s low price point and seemingly high feature set aims to have something for you.
Before getting into specifics, let’s run down the basics of ClearBox. It is a Win32 application that can run on Windows 2000/XP/2003. Other comparable servers are supported among multiple platforms, including Linux and Mac OS X, in addition to Windows. ClearBox is all GUI based; no command-line configuration is necessary. Like many other servers, it can handle RADIUS proxying and double-logon prevention. Although it lacks a server replication feature to easily implement a secondary server for back up reasons like other solutions do, it does offer integration with billing systems. XPerience Technologies says it should release an update in several months to include server replication.
Realm and Dynamic Configuration
We started the review by looking at its overall configuration scheme. Like other advanced RADIUS servers, ClearBox is configurable by realms. Each realm can have its own supported authentication protocols, user databases, authorization and accounting settings. Matching rules and username rewrite features enable you to set up which realm is selected when an authentication request comes in. For example, ClearBox can consult ActiveDirectory for usernames ending with @mainoffice, while for usernames ending with @secondaryoffice, account credentials could be checked against the internal database.
Though the settings for RADIUS clients, like realms, can be stored in databases and can be dynamically chosen when requests come in, the RADIUS clients are global. You cannot, for example, have a different set of RADIUS clients for each location or realm. Hence, the shared secret for APs with the same IP address must be the same. Since it is more secure to use unique shared secrets, this is a problem if using the same addressing scheme among multiple locations. However, we have yet to say that we haven’t came across a RADIUS server yet that supports this per-location client scheme.
Supported Authentication Protocols and Sources
As you can see in Figure 1, ClearBox sports the most popular EAP implementations for WLAN security:
- Protected Extensible Authentication Protocol (PEAP)
- EAP-Transport Layer Security (EAP-TLS)
- EAP-Tunneled Transport Layer Security (EAP-TTLS)
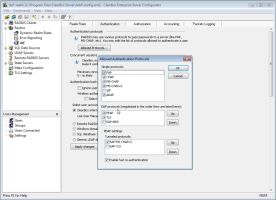 |
| WLAN security options |
The two unsecure Cisco implementations, Lightweight Extensible Authentication Protocol (LEAP) and EAP Flexible Authentication via Secure Tunneling (EAP-FAST), aren’t supported. Although other comparable servers include these outdated protocols, most won’t have to worry since they’ll have equipment that supports the more secure ones.
Like the majority of other RADIUS servers that enable wireless encryption, ClearBox supports other non-wireless authentication protocols:
- ASCII
- PAP
- CHAP
- MS-CHAP/MS-CHAPv2
- ARAP
- SIP-Digest
Now that we knew what type of authentication is possible, we wanted to see what methods could be used to retrieve the credentials of users and RAIDUS clients (APs) that authenticate through the server. ClearBox supports an abundance of databases and back-end systems; not only for the user accounts and RADIUS clients, but also for the server’s configuration. This freedom of how all the data is stored and retrieved makes this server very dynamic and creditable for advanced, carrier-class, schemes as well as the basic setups of small businesses.
In addition to its internal user manager and RADIUS client list, ClearBox specifically supports the following SQL-compliant data sources for user and client authentication:
Additionally, the following LDAP server types are supported for user authentication:
Authorization Features
ClearBox supports a range of authorization features. The more raw way of going about configuring authorization functions is to set policies on four different authorization lists as shown in Figure 2.
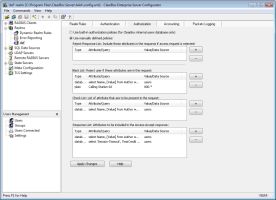 |
| Authorization features |
The black and check lists, respectively, allow you to specify what attribute (such as the Calling-Station-ID or MAC address) should not or should be present in the request packet from the client (AP). The Response List lets you add attributes, such as a VLAN assignment, to the response packet sent from the server granting access to a user. The Reject-Response List allows you to add attributes to the rejection packet.
Creating these raw authorization policies in ClearBox may be overwhelming, at least at first, for people not knowledgeable in the nitty-gritty of RADIUS technology or SQL statements, such as small business owners. However, like in most cases, the less user friendly solutions are, the more robust and feature-rich they are; you could stay the same applies here. We should also add that from ClearBox’s documentation, discussion forum and the support team, you probably won’t have a hard time finding examples for policies. For example, you can pretty much copy and paste in SQL commands for assigning users to VLANs or limiting wireless access based upon time constraints.
ClearBox’s recent update adds another, easier, way to enable authorization policies in a user friendly way. Using the User Management component with the internal database, you can define an activation and expiration date for user accounts, enforce login hours, assign time credits, restrict users to a device’s MAC address and more. These settings can be per user or per group. Figure 3 shows some of these settings.
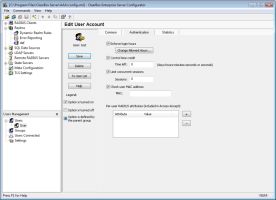 |
| User management settings |
Accounting and Billing
Lastly, we reviewed ClearBox’s accounting and billing aspects. In this area, we also found ClearBox highly configurable and customizable. The easiest route is to leave the default settings as is to log accounting information to the internal database, such as the username, session time, bytes in and out, and IP address. As Figure 4 shows, you can customize the extract attributes to log, or even the SQL Insert commands, to fit your particular needs.
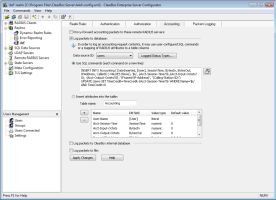 |
| Accounting and billing |
For customers running an ISP or charging the end users, ClearBox is completely interoperable with four third-party billing systems.
Configuring the RADIUS Server
After a simple, no thrills, installation of the server software, we selected to use the Configuration Wizard to help us set up ClearBox. For customers new to RADIUS, the wizard offers a simple but informative tutorial on the main components of a RADIUS environment. The wizard also helped us add the details (IP address and shared secret) of our RADIUS clients (APs) to ClearBox. Additionally, it helped us select to use the internal database for our settings.
After completing the Configuration Wizard, we found we needed to do a few more things before we had it set up to do the authentication for the WPA/WPA2-Enterprise network. We brought up Configurator and enabled 802.1X support with a quick click of a checkbox on the TLS Settings page. Then we needed to load the server with a digital certificate, so the clients can authenticate the server, as required by the PEAP protocol we wanted to use for user authentication. All we had to do is hit the Certificate Wizard button and follow it to create a new root Certificate Authority (CA).
After applying the certificate to the server, we needed to install the root CA onto our Windows computers, since we were using the wizard to create self-signed digital credentials rather than purchasing them through a real CA like VeriSign or GoDaddy. To do this, we brought up the Certificate Wizard again so we could export the root CA for our clients. Then we took the certificate file around to our Windows machines and installed it into the Trusted Root Certification Authorities certificate store.
Next, we added a user to ClearBox using the User Manager. Then it was time to configure our APs with the IP address of the server and the shared secrets. After configuring our Windows computers with the proper 802.1X authentication and WPA-Enterprise encryption settings, we were able to connect. Thanks to ClearBox we had a highly secure wireless network.
Our Final Words
Despite finding a few improvements that XPerience Technologies could make, we believe they’ve created a well-balanced RADIUS server. ClearBox Enterprise RADIUS Server 2.3 hit on the principal attributes we were looking for: feature-rich, customization, and user-friendly. In the end, we believe that we came across a great server that can provide, among other authentication services, the 802.1X requirement for implementing enterprise-level WPA or WPA2 encryption for Wi-Fi networks.
Take ClearBox on a test drive! You can download a 30-day fully functional trial.
Product: ClearBox Enterprise RADIUS Server
Vendor: XPerience Technologies
Price: $599
Pros: priced low, feature-rich, highly customizable
Cons: No Windows Vista or cross-platform support, lacks server replication, only globally defines RADIUS clients
Eric Geier is the Founder and President of Sky-Nets, Ltd., a Wi-Fi Hotspot Network. He is also the author of many networking and computing books, including Home Networking All-in-One Desk Reference For Dummies (Wiley 2008) and 100 Things You Need to Know about Microsoft® Windows Vista (Que 2007).

