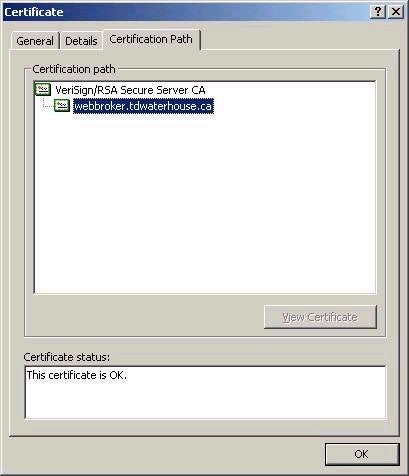
An important consideration when choosing the type of CA is the environment and the way in which you intend to use the certificates. If it is strictly for internal use, then your options are wide open according to your environment (for example is you have AD, then use you can use either Enterprise or Standalone CAs). If however you need certificates to secure a public website, then an external certificate authority will need to be involved, either providing the certificates for that site directly, or via a chain of trust. For example, if you access a secure website and click on the lock icon on the bottom left of the Internet Explorer window, you can view the Certification Path for that site, as shown below.
Installation of Certificate Services
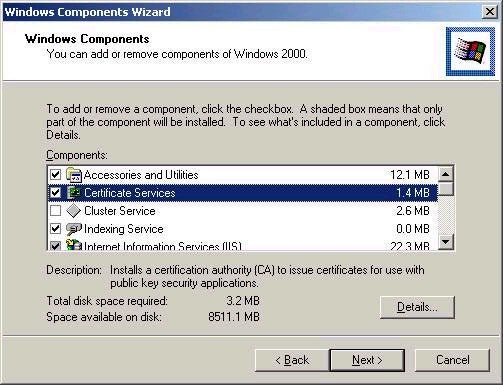
Installing Certificate Services on Windows 2000 is quite simple, though the choices available to you will again depend on your environment. For the purpose of this illustration I will walk through the process of creating a Standalone Root CA – mainly because my computer is not configured as a domain member at the moment. Since it is not installed by default, you will need to add Certificate Services using the Add/Remove Programs – Windows Components option in Control Panel, as shown below:
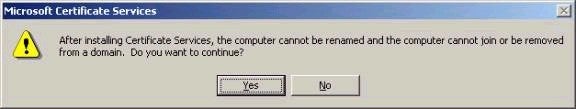
Note that when you attempt to choose Certificate Services, you
will be presented with the dialog box shown below. Note
the fact that you will not be able to rename the system or
join or be removed from a domain without first
uninstalling Certificate Services.
After choosing Next, you will be asked to decide what type of CA
you wish to create. Note that my system has only the
Standalone CA options available, since it is not a member
of an Active Directory domain.
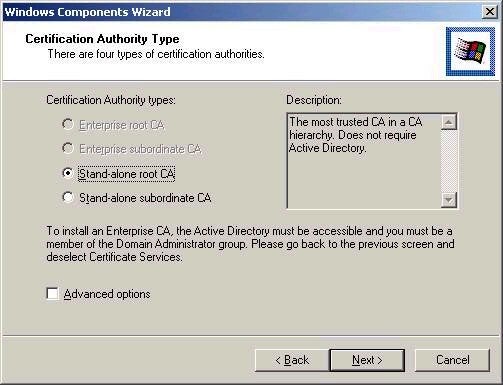
Note that the Advanced options
checkbox on the screenshot above will allow you to choose
advanced cryptographic options in the key generation
process. I would suggest allowing the default values to be
used unless you are certain of the need to make other
choices.
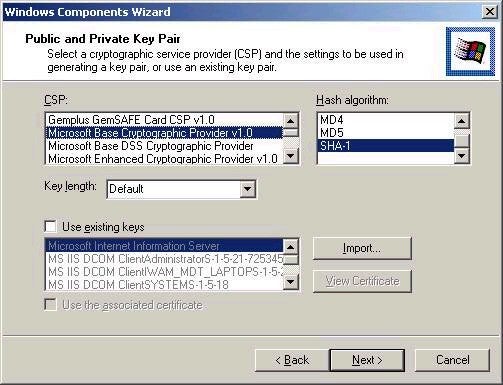
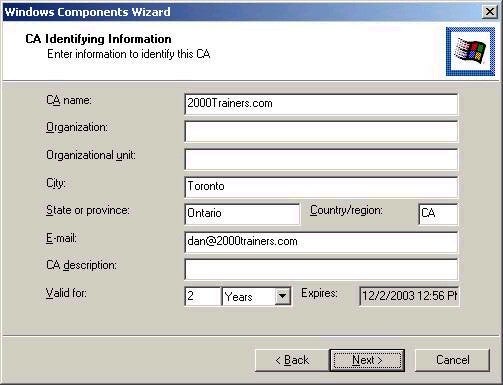
Clicking
Next again will bring you into the CA Identification
screen, where you should enter the appropriate
information. Note that while not all fields are mandatory,
they should be completed in full.
The final screen in the process asks for where you wish to
place configuration and logging data, as shown below.