In the
world of Windows administration, you will stumble on security quite frequently.
During my first job, it was funny to see how secret the local
administrator password was to the group. Nothing was held quite so
sacred.
In the world of Windows administration, you will stumble on security quite frequently. During my first job, it was funny to see how secret the local administrator password was to the group. Nothing was held quite so sacred.
Nothing has changed with Windows 2000, nor will it with the inception of XP — you will still need to manage the security in your environment, and it will still be a pain in the butt.
And now with the idea of user vs. machine and the introduction of Windows Installer and enterprise management, things have gotten even more confusing. So, let’s get back to the basics.
To access the security for your local machine, go to the Control Panel and then to Local Security Policy. You will be presented with the following:
Nothing
has changed with Windows 2000, nor will it with the inception of XP — you
will still need to manage the security in your environment, and it will still be
a pain in the butt.
And now with
the idea of user vs. machine and the introduction of Windows Installer and
enterprise management, things have gotten even more confusing. So, let’s get
back to the basics.
To access
the security for your local machine, go to the Control Panel and then to Local
Security Policy. You will be presented with the following:
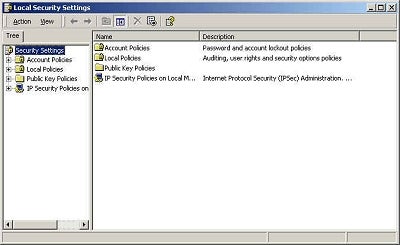
From
here, you can drill down into any of the folders to work with the security
policy on the machine that you are on. For example, here is how you would
restrict Password Policy:
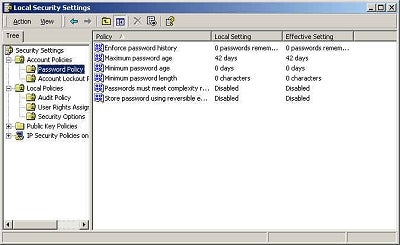
Whatever you want
to do with the security policy, this is where you will do it. You will want to allow
the local administrator all rights and, naturally, the system as well.
These
accounts are your most important…and the ones that you do not want anyone
messing with. Microsoft has a great article entitled “How the System
Account is Used”. You can get to it from the following link:
Let me
know if you have any questions about these accounts or security in general.

