Tools for Securing IIS
Use Windows Update and Automatic Updates for single-server installations.
Microsoft’s IIS and SQL Server can provide tempting targets for malicious people. Our security checklist will help you lower your risk of attack.
Use Systems Management Server (SMS) or Windows Server Update Services (WSUS)for managed environments or where administrators that have responsibilities for multiple disparate systems.
Microsoft Baseline Security Analyzer (MBSA)assists the system administrator in scanning local or remote systems for current patches. This tool works on Windows NT 4, Windows 2000, Windows XP and Windows 2003.
Use the IIS Lockdown Toolor Security Configuration Wizard (SCW) to harden your IIS installation and server. Use URLScan to filter HTTP requests. URLScan is part of the IIS Lockdown Tool and can be configured to reject maliciously formed HTTP requests such as those in Code Blue and Code Red, before the server even attempts to process them.
Download these tools to another machine and copy them to your IIS server before connecting it to the Internet. Avoid connecting your IIS server to the Internet until it is completely analyzed and patched.
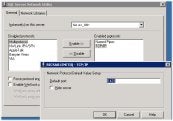 |
| Changing the Default Port SQL Uses (Click for a larger image) |
SQL Specific Security Recommendations
The most widespread SQL attack isn’t even covered by a security bulletin. It’s a straightforward login attempt made on the SA account with a blank password. Microsoft SQL Server installs with a blank SA account password by default and this should be the first thing you change.
Another common cause of the blank password is products. For example some versions of Visio install Microsoft SQL Server 2000 Desktop Engine (MSDE) and never change the SA password. A user may not even know that they have MSDE running. You can download a program from eEye Digital Securitythat scans your network for SQL Servers with blank SA accounts. .
SQL Server Security Checklist
- Set a password on your SA account and restrict its use. Also, change the password periodically to keep it from ‘propagating’ and being used by developers or too many administrators. Change the SA password if anyone who knows it leaves the company. Use eEye’s tool to scan your network for SQL servers with no SA password.
- Place your SQL Server behind a firewall, separate from your IIS or Web servers. Only allow connections to the SQL server from those designated web servers. Your SQL server should never be Internet-facing or publicly accessible.
- Remove BUILTIN/Administrators from the sysadmin role and give sysadmin rights in SQL to specific domain accounts that need it.
- Use Windows Authentication and Windows Only Mode if possible. This way, a potential hacker must authenticate to the domain first instead of just to SQL Server.
- Do not run SQL Server on a Domain Controller.
- Change the SQL Server service startup account to something besides LocalHost.
- Enable the Failed Login option (Server Properties | Security tab) so you can look for failed logins to see if an unauthorized person is trying to access the server. Monitor the SQL logs and set up alerts in SQL using NETSEND or email, if possible.
- Keep up to date on patches and service packs for the operating system and SQL. See Tools for Securing IISfor some options.
- Protect any Extended Stored Procedures. Control all data access through stored procedures and grant access to those instead of giving blanket db_datareader and db_datawriter permissions to the data itself. See Part Iof this article for more information.
- Change the standard SQL Server port under the Server Network Configuration Utility and block the default port of 1433. Have your network administrator allow the new port instead.
- Make sure the Everyone group doesn’t have write access to SQL Server registry keys.
Resources
- Microsoft Security Notification Service
- Technet Security Homepage
- SQL Server 2000 Security
- SANS Institute
- US CERT
Article appeared originally on EnterpriseNetworkingPlanet.com.

