| Tree
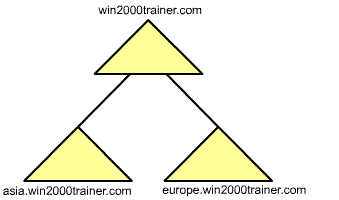
In Windows 2000, multiple domains may still be necessary, especially in large organizations where companies want to remain tight control over their environments, their own identities (such as different business units), and distinct administrative control. In Active Directory, a collection of domains can be created that form a hierarchy referred to as a tree. In a tree structure, domains fall into a parent/child relationship. That is, the new child domain takes on the domain name of its parent domain. For example, I might create separate domains for the European and Asian divisions of my company. If this were the case, I might end up with the tree shown below: |
|
|
| Note that each domain in the tree is a separate and distinct administrative unit, as well as a boundary for replication purposes. That is, if you create a user in the asia.win2000trainer.com domain, the account exists on domain controllers in that domain, and will be replicated to all other domain controllers in the asia.win2000trainer.com domain. Note also that each new child domain has a transitive two-way trust relation with its parent. This is configured automatically by Active Directory, and exists to allow users in one domain access to resources in another. Even without a direct trust, users in Asia can access resources (for which they have been given appropriate permissions) in the Europe domain and vice versa, since the trust relationship is transitive (Asia trusts its parent, who trusts Europe – therefore Europe trusts Asia and vice versa). A tree is broadly defined as a collection of domains that form a parent/child relationship and share a contiguous namespace.
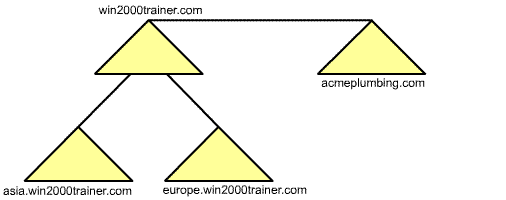
Forest Forest is the term used to describe a collection of Active Directory trees. Each tree in a forest has its own distinct namespace. For example, lets say that my company owned another smaller company called Acme Plumbing. If I wanted Acme Plumbing to have its own distinct name and domain, I might end up with a collection of trees, forming a forest, as shown below: |
|
Welcome to article 8 in my 70-240 in 15 minutes a week series. This week’s article is the first in our look at the Windows 2000 Server portion of the exam – it covers an introduction to both Windows 2000 Server as well as Active Directory concepts…
|
| The acmeplumbing.com domain is part of the same forest as the win2000trainer.com domain tree, but is still its own domain and tree. Note that there are transitive trust relationships between the root domains of every tree in a forest – this allows acmeplumbing.com users to access resources in the win2000trainer.com tree and vice versa, while allow them to maintain distinct identities. Note that the first domain created in a forest is considered the forest root. One important feature of a forest is that every single domain shares a common schema – the definition of the different types of objects and associated attributes that may be created with the forest. It is also important to recognize that a forest might be made up of a single tree, containing a single domain. It may be small, but technically it is still a forest!
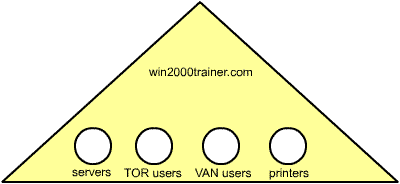
Organizational Unit An organizational unit (commonly referred to as an OU) is a container object within Active Directory used to group objects for the purposes of delegating administrative authority and the application of group policy within a domain. OUs can be created to organize objects in a number of ways, including according to function, location, resources, and so forth. Example of objects that can be grouped into OUs would include user accounts, computer accounts, group accounts, and so forth. The diagram below outlines an example OU structure based on user location and resources: |
|
|
| Note that an OU can only contain objects from the same domain in which it exists. Also note that OU structures will vary widely from company to company. They are meant to be designed with administration of resources and the application of group policy settings in mind. Since complete administrative control can be granted (delegated) to a user over an OU and potentially nothing else, it makes it possible for a very large organization to have only a single domain, which each business unit having administrative control over their own OU only. |