How to Secure Virtual Machine Access using DACLs
Authorization Manager, which will be discussed in a future article in this series, is the main tool for securing virtual machine access. You can also configure DACLs on the virtual machine folder to provide security to virtual machines running on the Hyper-V. This is basically done by applying the NTFS permissions.
 |
| Securing Virtual Machine Access Using DACLs |
When deploying virtualization technologies, key choices must be made to ensure the environment is secure. This article explains how to use Authorization Manager to make Hyper-V as secure as it can be.
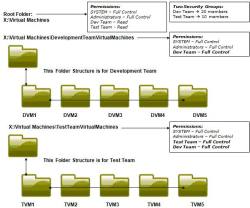
As you can see in the above figure, an organization has two teams: development and test. Two security groups are already created for these teams — Dev Team and Test Team. The Development Team is responsible for designing the codes and then handing them over to the Test Team for testing. The Development Team must access all 10, for example, virtual machines. At the same time, they must make sure the Test Team does not have access to their virtual machines, except TVM1 through TVM5. To achieve this, assign the NTFS Permissions on the virtual machine folders.
In this example, there are three virtual machine folders:
- X:Virtual Machines
- X:Virtual MachinesDevelopmentTeamVirtualMachines
- X:Virtual MachinesTestTeamVirtualMachines
Dev Team Security Group is assigned full control permissions on 2 and 3 folders. On other hand, Test Team is assigned Full Control permissions only on 3 folder. Test Team does not even have Read permissions on 3.
Hyper-V Services Overview & Securing Hyper-V Services
Hyper-V is a client/server application. Hyper-V comes with three services by default, as mentioned below:
| Service Name | Functions | Security Context | Recommendation Configuration |
| Virtual Machine Management Service | Manages overall Hyper-V environment | SYSTEM Account | Default |
| Hyper-V Image Management Service | Management of Virtual Hard Disks | Network Service | Default |
| Hyper-V Network Management Service | Management of Hyper-V Virtual Networking | SYSTEM Account | Default |
The services shown above are configured to start automatically under the security context of SYSTEM Account. The account under which these services run has got the highest privileges on the system. You should never change the account under which they run. If you do so, a hacker or malicious can cause harm to virtual machines or Hyper-V Parent Partition. The SYSTEM account password is not known by a malicious code or hacker. It is not safe to run these services under a domain user account, as a malicious user or hacker might try to get the password using the brute force applications.
Conclusion
This article explained how Hyper-V stores VHDs and XML files on the system drive. It is always recommended to change the default location for storing VHDs and XMLs to a SAN Drive and then provide the security by assigning NTFS Permissions. We also provided an example of how to secure virtual machine access using the NTFS Permissions.
The later part of this article will explore:
- Hyper-V Firewall Rules and Configuration
- Securing Hyper-V & Virtual Machines using Authorization Manager
- An example to provide Hyper-V Security using Authorization Manager
- Hyper-V Security Best Practices

