

Static Application Security Testing (SAST) is often used to scan the source, binary, or byte code of an application. As well as identifying the root cause of vulnerabilities, it helps to remediate any underlying security flaws and provides feedback to developers on any coding problems. The major benefit is to have more code created with fewer vulnerabilities.
Read more: Top 5 Cybersecurity Certifications to Advance Your Career
ServerWatch evaluated many SAST tools. Here are our top picks in no particular order.
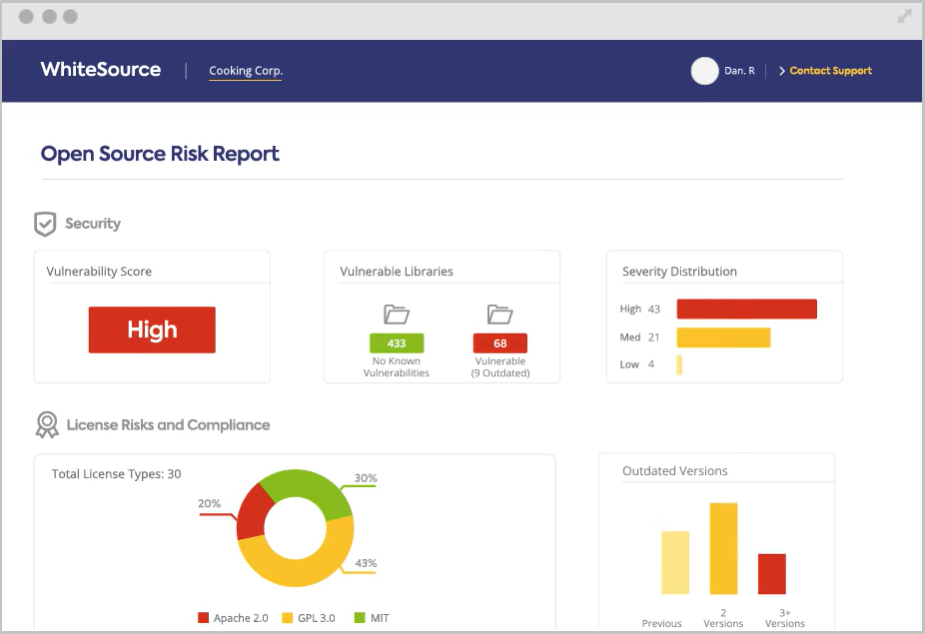
WhiteSource Cure is a security auto-remediation application designed for custom code. It replaces vulnerable code with fixed secured code by offering developers remediation suggestions for security vulnerabilities. WhiteSource Cure offers a remediation-centric approach that goes beyond detection, acting as a developer’s security expert to help speed up the release of secure software.
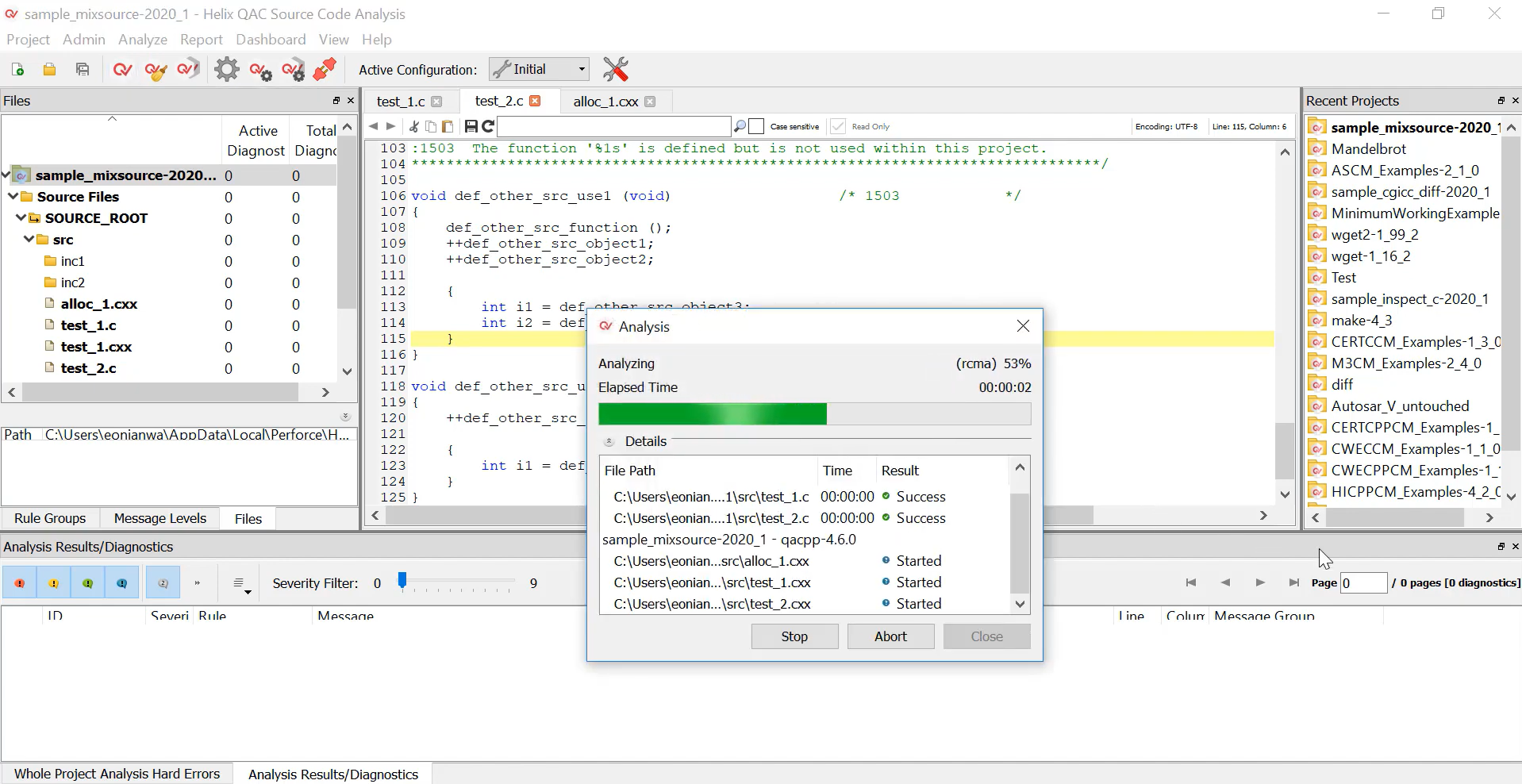
Perforce SAST offerings consist of two tools, Klocwork and Helix QAC. These tools provide developers complete coverage of coding standards, security compliance, and safety compliance. Perforce SAST tools support most of the development languages, including C, C++, C#, Java, JavaScript, and Python. Developers can use the SAST tools within their IDEs like visual studio code, IntelliJ, and others.
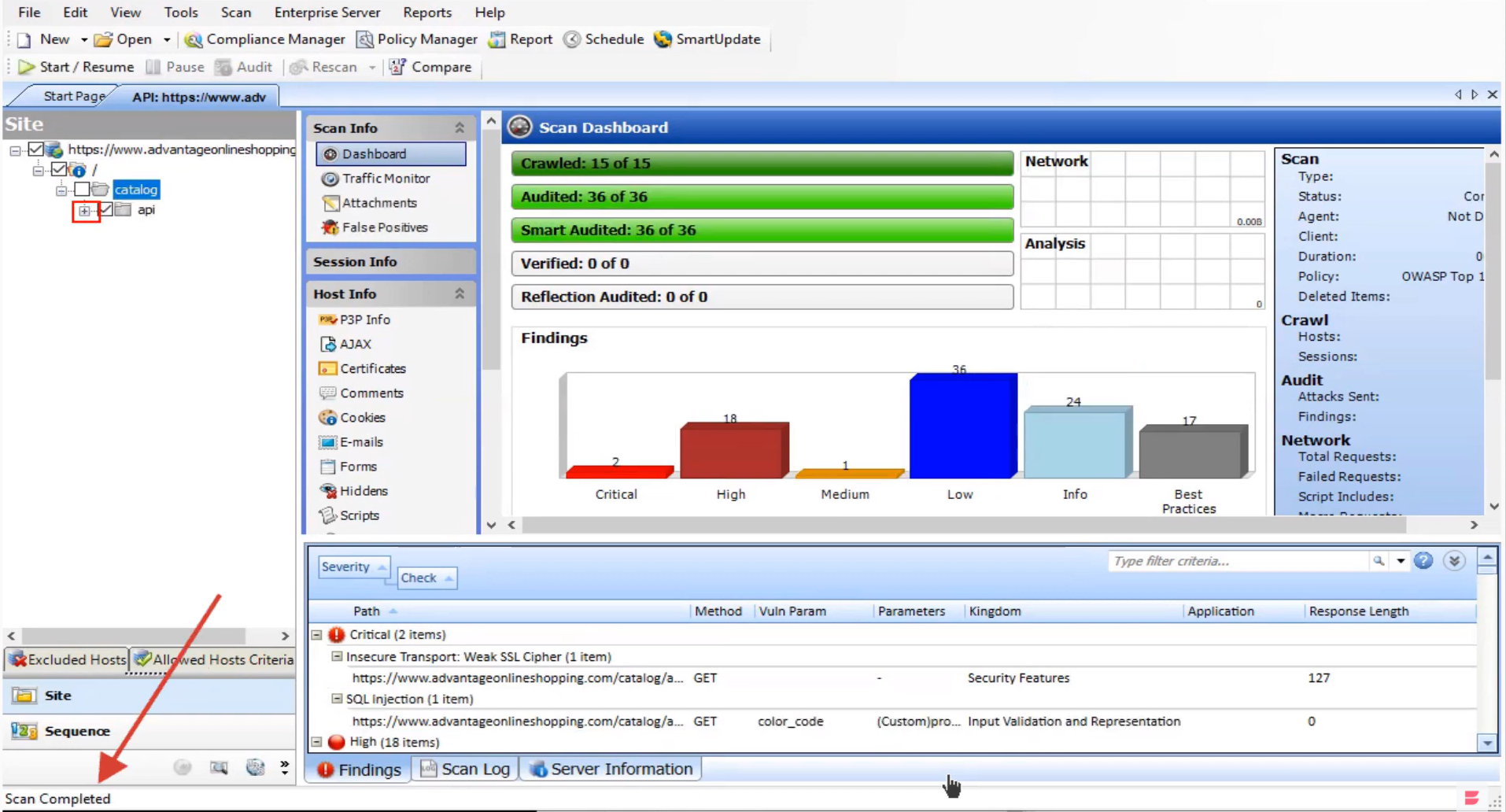
CyberRes Fortify includes both static and dynamic application security testing technologies, along with runtime application monitoring and protection. Developers can use the SAST tool to find and fix security defects in real-time during the coding process, with integrations to IDEs such as Eclipse or Visual Studio.
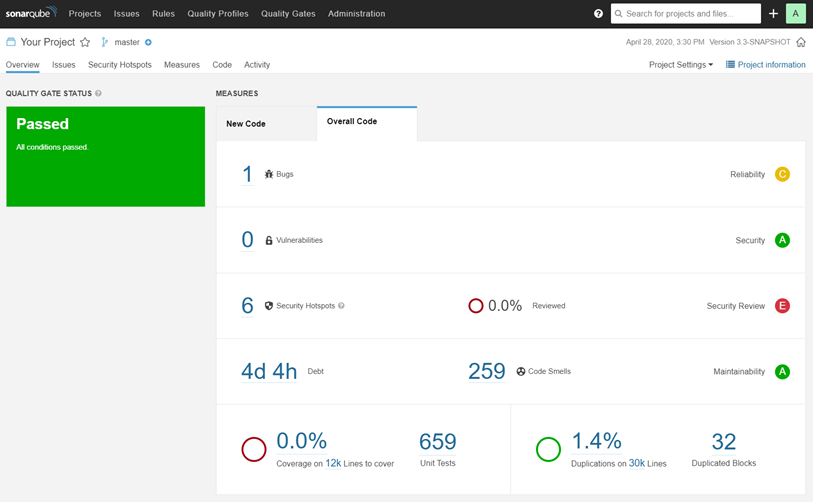
SonarQube empowers developers to write cleaner and safer code. It encompasses an open-source community of more than 200,000 development teams. Thousands of automated Static Code Analysis rules protect apps.
SpectralOps scans the entire SDLC for hard-coded secrets, keys, and misconfigured code, continuously. It is a multi-language AI-driven SAST. The primary objective is to prevent secrets (credentials, API keys, encryption keys, etc.) from leaking, as they tend to be hard-coded at the early stages of development.
Checkmarx supports many languages out of the box with no configuration. It identifies security issues and offers solutions. With Checkmarx SAST, you can run fast incremental or full scans whenever needed.
Veracode Static Analysis for SAST has a low false-positive count and offers developers potential solutions to issues it finds. As it is a Software-as-a-Service solution, there is low setup overhead and a quick turnaround from acquiring access and getting results.
Reshift is a more specialized SAST offering, specifically built for NodeJS. The approach is to fix errors as early as possible. By integrating into IDEs and CI/CD pipelines, Reshift makes sure to test code as soon as it is typed.
Read more: Best Server Security Services
SAST is a mature application security testing method, where source code is analyzed from the inside out while components are at rest. It scans in-house code and design to detect flaws that are indicative of weaknesses that could lead to security vulnerabilities.
SAST doesn’t scan dynamic code. It focuses on static code and tests code at rest, without having to run it. That makes it easy to use at the coding and testing stages of development, integrating into Continuous Integration (CI) servers and, more recently, into integrated development environments (IDEs).
The scans done by SAST tools are based on predetermined rules that define coding errors to assess and address. These scans are very good at identifying common security vulnerabilities such as SQL injection, input validation, and stack buffer overflows.
SAST has limitations, however. It is good at finding problems within the code, but not vulnerabilities outside the code in areas such as APIs. That requires a different approach known as Dynamic Application Security Testing (DAST). There are also other related tools known as Mobile Application Security Testing (MAST), and Interactive Application Security Testing (IAST).
SAST methods are generally used early in the development cycle to test the application from the inside out (also known as white box testing). No need to have perform the code analysis on a running system; these tools test line-by-line.
DAST, on the other hand, is a black box testing approach that is done while the application is running, taking an outside-in approach. DAST makes attempts to penetrate the application to identify vulnerabilities. Its testing encompasses bugs outside the code and in third-party interfaces, source code, byte code, and binaries — which usually makes such analysis easier to use and less expensive than SAST.
However, DAST tools may not be able to isolate the exact site of a weakness in the code. Thus, it is probably best to adopt a hybrid analysis testing method that combines both SAST and DAST.
Read next: Top DAST Tools: Dynamic Application Security Testing
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.