

Since OpenVPN uses SSL encryption, you must create and install SSL certificates on the server and clients. Choose a secure PC on which to create and manage your PKI (public key infrastructure), and then download and install OpenVPN using the Windows Installer. Remember, you may need to come back to this PC to create additional client certificates in the future.
Building a VPN? Tomato Router is one way to bypass expensive equipment to give users secure remote access or connect offices.
Once OpenVPN is installed, you can get started:
Next, go to the following directory in Windows: C:Program FilesOpenVPNeasy-rsa. Then right-click the vars.bat file and click Edit. You must change the default values of all the following settings:
 |
| Tomato VPN Router Configuration Files (Click for larger image) |
If the file opens in Notepad, there probably will not be any line returns, and everything will be run together, which is fine. Be sure edit only the setting values between the equals sign and the word “set”. For a better visual, you can download and use an editor like VIM.
Now go back to the Command Prompt window and initialize the PKI by entering the following commands one at a time:
vars
clean-all
build-ca
|
You’ll be prompted (see Figure 3) for the parameters you just set in the vars.bat file; hit Enter to accept them. You can leave the Organizational Unit Name blank. However, you must enter a Common Name. This will be the name of the CA certificate that will be installed onto the server and all the clients. You might pick something like “ABC_Corp-VPN-CA”
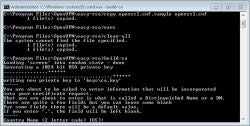 |
| Figure 3 Tomato VPN Router Parameters (Click for larger image) |
Now you can create a certificate and private key for the server with this command:
build-key-server server
|
You’ll be prompted for parameters again. Accept the defaults for the ones you set in vars.bat. For the Common Name, enter something like “ABC_Corp-VPN-Server”. Be sure to enter a secure password you’ll remember or store somewhere safe. When prompted to sign and commit the certificate, confirm the details and then enter “y”.
Next, you can create the client certificates for the computers or routers that will be remotely connecting to your VPN server. You must create a separate certificate for each client. Enter “build-key” into the Command Prompt, followed by a space and a name for the certificate. For example, for three clients:
build-key client1
build-key client2
build-key client3
You might want to be more descriptive with the name, specifying the person or router that will be using it.
You’ll be prompted for the parameters once again. Choose a unique Common Name for each, which you might want to be the same as the certificate name. You can optionally create a password.
Note: If you must generate additional client certificates in the future, return to the easy-rsa directory in a Command Prompt, type “vars”, and then go ahead with the build-key command, such as build-key client2.
Now you must generate the Diffie Hellman parameters by entering:
build-dh
|
Finally, you should see all your certificates in the following directory: C:Program FilesOpenVPNeasy-rsakeys
Keep in mind; the CA, server, and all client keys should be kept private and secure.
Stay tuned–in the next part, we’ll configure the VPN server and clients.
Eric Geier is the founder and CEO of NoWiresSecurity, which helps businesses easily protect their Wi-Fi with enterprise-level encryption by offering an outsourced RADIUS/802.1X authentication service. He is also the author of many networking and computing books, for brands such as For Dummies and Cisco Press.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.