There have been several improvements to the IIS 6.0 security model. One of the factors that has been a concern with previous version of IIS is default configuration. IIS was installed and enabled by default in Windows 2000 Server family installations. This caused problems when exploits were released and people were affected without realizing that IIS was even installed. Microsoft has taken several steps to decrease the attack surface of IIS significantly. IIS 6.0 is not installed by default on Windows 2003 Server family installations. When IIS 6.0 is installed, it is configured in a locked-down state. It is little more than a static content Web server. You must enable Web service extensions in order to service dynamic content. ( figure 4 ) In this example I have enabled ASP.NET, ASP Classic, and server-side includes.
Figure 4.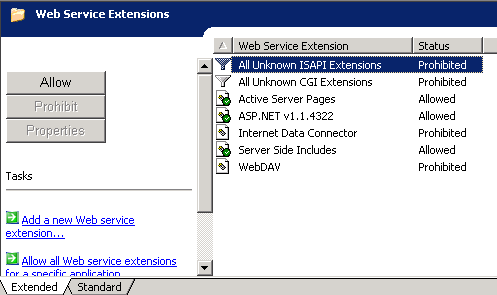
In addition, both ASP Classic and ASP.NET have been configured to run under the lowest privileged account possible. Some other improvements include disabling the ability to install IIS via group policy, disabling of IIS on upgrade, buffer overflow detection, and write protection for content. IIS 6.0 also allows configurable identities for each worker process.
Authentication and Authorization
Authentication and Authorization are often confused with each other. Authentication is the method of defining who you are, and authorization determines what privileges you have. With ASP.NET Microsoft has implemented a new authentication method focused on their Single Sign On goals. IIS 6.0 now supports native Passport integration. A Passport account can also be mapped to a Windows account. Authorization has been vastly revamped as well. In the past authorization has been utilized as ACL (Access Control Lists). The problem with this method is that it is very object driven, focused on files, directories, etc … . Most Web-based applications are more task or operation based. The new authorization framework with Windows 2003 Server provides a solution. IIS 6.0 uses this tool by providing gatekeeper authorization to specific URLs. Web applications can also use URL authorization in tandem with the Authorization manager to control access from within the same policy to control application specific tasks or operations. Constrained, Delegated authentication is the last security feature. Delegation is the act of letting a server impersonate as a user on the network. This allows Web applications to act as a network user for the purpose of gathering information from another server in the enterprise and bringing it back to the Web server in a consolidated manner. Configured correctly this can be a very powerful tool in designing application suites because applications can make use of RPC or DCOM. There are a few caveats with this feature, such as malicious server administrators impersonating clients to gain access to unauthorized servers and services.
In order to improve scalability many applications have moved to a clustered or Web farm model. This can prove difficult from a management and administrative point of view in a large environment. Microsoft has added several features to improve the manageability of multiple servers. In previous version of IIS, the metabase has been configured as a binary store of settings. While there was an IIS Admin object model to access this configuration store, it often proved ungainly for the average administrator. The metabase has been converted to a plain text, human readable XML file for configuration with IIS 6.0. The metabase supports historical change versioning, meaning if the metabase is changed and saved, IIS automatically makes a copy of the original metabase and copies it into a history folder. This makes rollback operations of Web servers very easy. Another feature is the ability to modify the metabase while the Web services are running. An administrator can modify settings, such as creating a virtual directory, while the Web site is operational. When the file is saved, the changes are automatically detected and validated, and if valid, applied to the Web server with no restart or recompilation. This significantly improves uptime for configuration changes.
I hope I have been able to convey the very exciting improvements made to the Microsoft Internet Server platform with IIS 6.0 and Windows 2003. I feel Microsoft has made leaps and bounds with this new version. I look forward to working with this technology in the future.
About The Author
Jeff Gonzalez has been involved in software development for over seven years. Jeff’s diverse background has seen him working across North America in projects ranging from high volume commerce infrastructures to customer and employee management systems. Highly specialized in Microsoft solutions, Jeff has played key roles for leading companies like Microsoft, Rare Medium, Penson Financial, and city of Fort Worth. He is currently lending his talents to a company called Third Coast Media, developing custom software solutions for the automotive industry. He can be contacted at jeff@objectfoundry.com.
Property of TechnologyAdvice. © 2026 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.