
IPSec
Windows 2000 supports IPSec, which can provide for secure network communication between clients by encrypting IP-based data and using Kerberos for authentication. The beauty of IPSec is that is not application-based encryption (which would require that an application on both the sending and receiving computer supported encryption) but rather network-stack based. As such, any TCP/IP-based application is capable of utilizing IPSec, because encryption (and decryption) actually happens in the protocol stack. As such, the encryption is completely application-independent and totally transparent to the user. A diagram of IPSec with relation to the TCP/IP protocol stack is shown below:
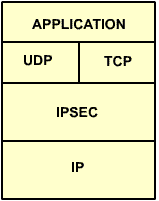
Windows 2000 supports IPSec in two modes – transport mode and tunnel mode. In tunnel mode, two endpoints (IP addresses) must be defined, and IPSec will encrypt data (it can also be used for authentication of systems only) that travels through the tunnel. This setup is commonly used in connecting remote offices via VPNs over the Internet. Note that the systems communicating need not necessarily be Windows 2000-based, since IPSec is an open standard. In transport mode, policies can defined which designate when and how IPSec encryption should be used on the network. For example, you could specify that only traffic moving from a client to TCP ports 80 or 23 on a server must be encrypted, and that all other traffic need not be. Similarly, you could specify that a client must initiate encrypted communication with a server or the server will not respond. The level and degree of IPSec use on your network is only dictated by your own needs (don’t forget that any encryption will create CPU overhead).
IPSec is controlled on Windows 2000-based system via security policies. Again, these can be configured either locally or via group policy (recommended). At any given time, only one IPSec policy can be assigned to a system. Although you can create custom IPSec policies, three are provided by default (as shown below) and you should be aware of their purposes.
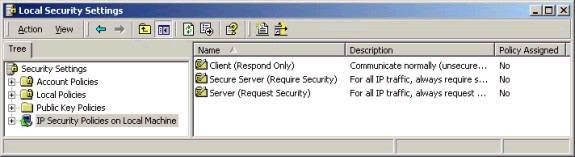
Client (Respond Only) – When this policy is assigned, a client will never initiate a secure connection with a server, but will use IPSec if requested to do so by a server.
Secure Server (Require Security) – When this policy is assigned, a server will drop any request that is made to it that does not use IPSec.
Server (Request Security) – When this policy is assigned, a server will request that a client has made an unsecured connection use IPSec. If the client is not capable (for example a Windows 98 system), the server will allow the connection to proceed, without requiring IPSec to be used.
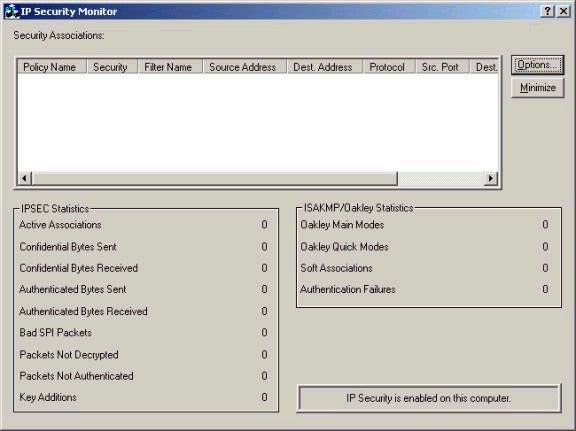
Note that none of the default policies if assigned by default, and that right clicking and choosing ‘Create IP Security Policy’ can create customized policies. The IP Security policy wizard will walk you though the steps of creating a custom policy, but you must be aware of the filters you are going to configure, including which port numbers are used by applications and so forth. Note also that Windows 2000 provides an application for troubleshooting and monitoring IPSec-based communications, The IP Security Monitor (ipsecmon.exe) as shown below.
And finally the Windows 2000 Server section of the series is complete. Remember that in order to save time, much of the material from the Server and Professional portions of the exam were not repeated. As such, if you are studying for either exam individually, you sure be sure to read all of the Server and Professional articles instead of either section individually. Next week begins the Active Directory Administration and Implementation portion of the series. I’m probably as happy as you are to be finally done with the Server and Professional stuff. I want to again thank everyone for your support of the series – it has been great. Please be sure to visit my website
http://www.win2000trainer.com to check out my free practice exams, with now over 25 available. Also, please consider posting technical questions to my message board instead of emailing them to me directly – this way many people will benefit from both the questions and answers provided. As usual, feel free to email me with your questions and comments; I look forward to hearing from you! Best of luck with your studies this week.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.