

Endpoint detection and response (EDR) is all about securing and monitoring all enterprise devices to effectively detect and respond to potential incursions. With so many servers, PCs, laptops, tablets, and smartphones accessing enterprise networks, an EDR tool is necessary to keep on top of things.
Endpoint detection and response (EDR) is about collecting and analyzing data from endpoints regardless of where they are in the network — in-house, remote, or mobile. The goal is to spot and stop attacks. As well as removing threats, EDR can help to trace the source of any attacks, so that such events can be prevented in future.
In essence, EDR software provides a central hub to manage organizational endpoints. The good ones can spot and stop attacks long before a human becomes aware of them.
Read more: Best Server Security Tools
There are a large variety of EDR solutions and services to choose from. Here are some of the best endpoint security tools, in no particular order.
Sophos Intercept X synchronizes native endpoint security with server, firewall, and email security. It provides a holistic view of an organization’s environment with a rich data set and deep analysis for threat detection, investigation, and response. Sophos Intercept X employs a comprehensive defense-in-depth approach to endpoint protection, rather than relying on one primary security technique.
This layered approach combines modern and traditional techniques to stop a range of threats. It uses AI to detect and block malware by scrutinizing file attributes from hundreds of millions of samples, identifying endpoint threats without the need for a signature.
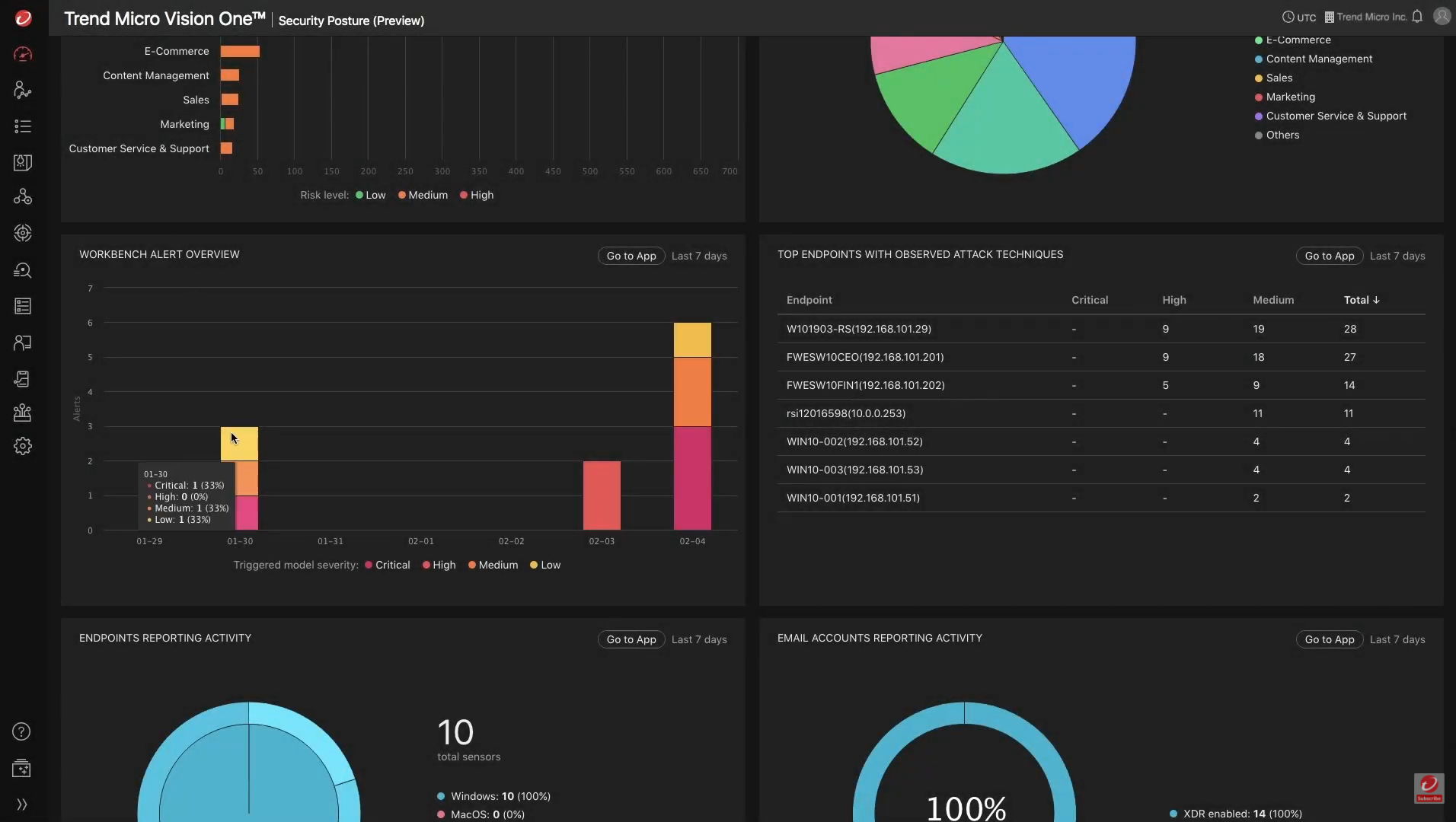
Trend Micro Vision One provides EDR capabilities across email, endpoints, servers, cloud workloads, and networks. It is a purpose-built threat defense platform that provides extended detection and response (XDR) capabilities to collect and automatically correlate data across multiple security layers. It prevents the majority of attacks with automated protection.
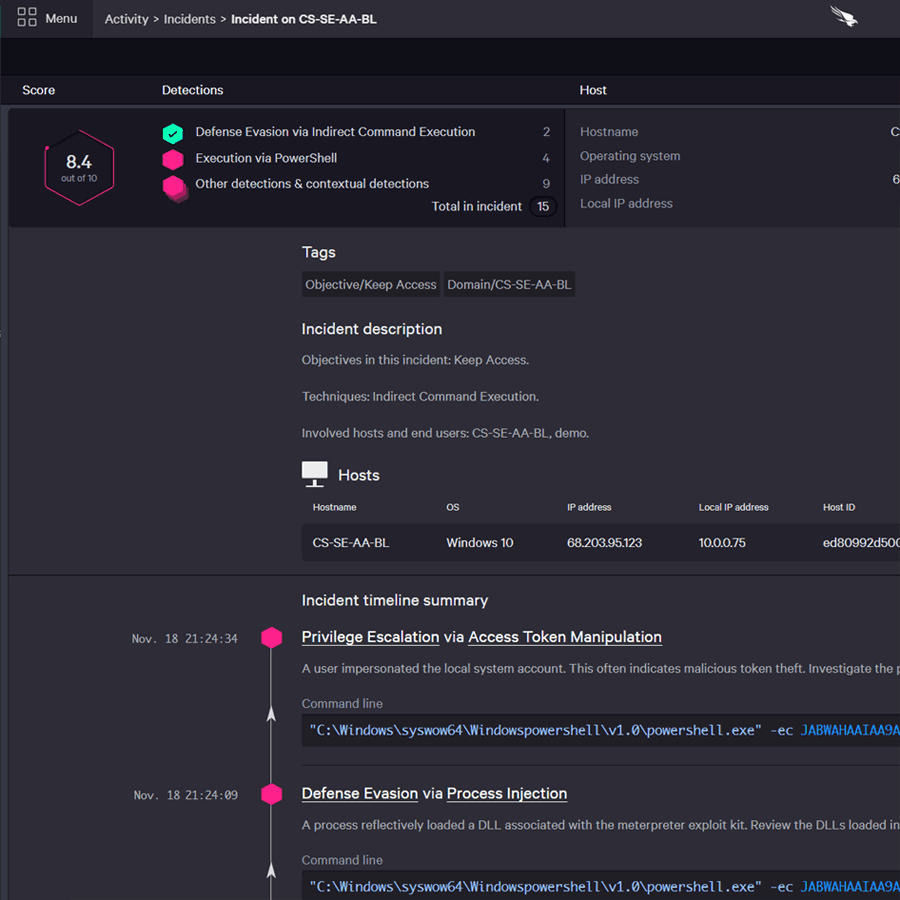
CrowdStrike offers Falcon Insight as an EDR software solution. It delivers continuous endpoint visibility that spans detection, incident response, and forensics to ensure nothing is missed and potential breaches are stopped. It continuously monitors all endpoint activity and analyzes the data in real time to automatically identify threat activity, enabling it to both detect and prevent advanced threats as they happen.
Ivanti Neurons for Unified Endpoint Management (UEM) offers visibility into the entire asset estate, bringing in mobile devices and combining them with traditionally managed devices. It enables a higher level of automation, as well as a single source of truth for all devices.
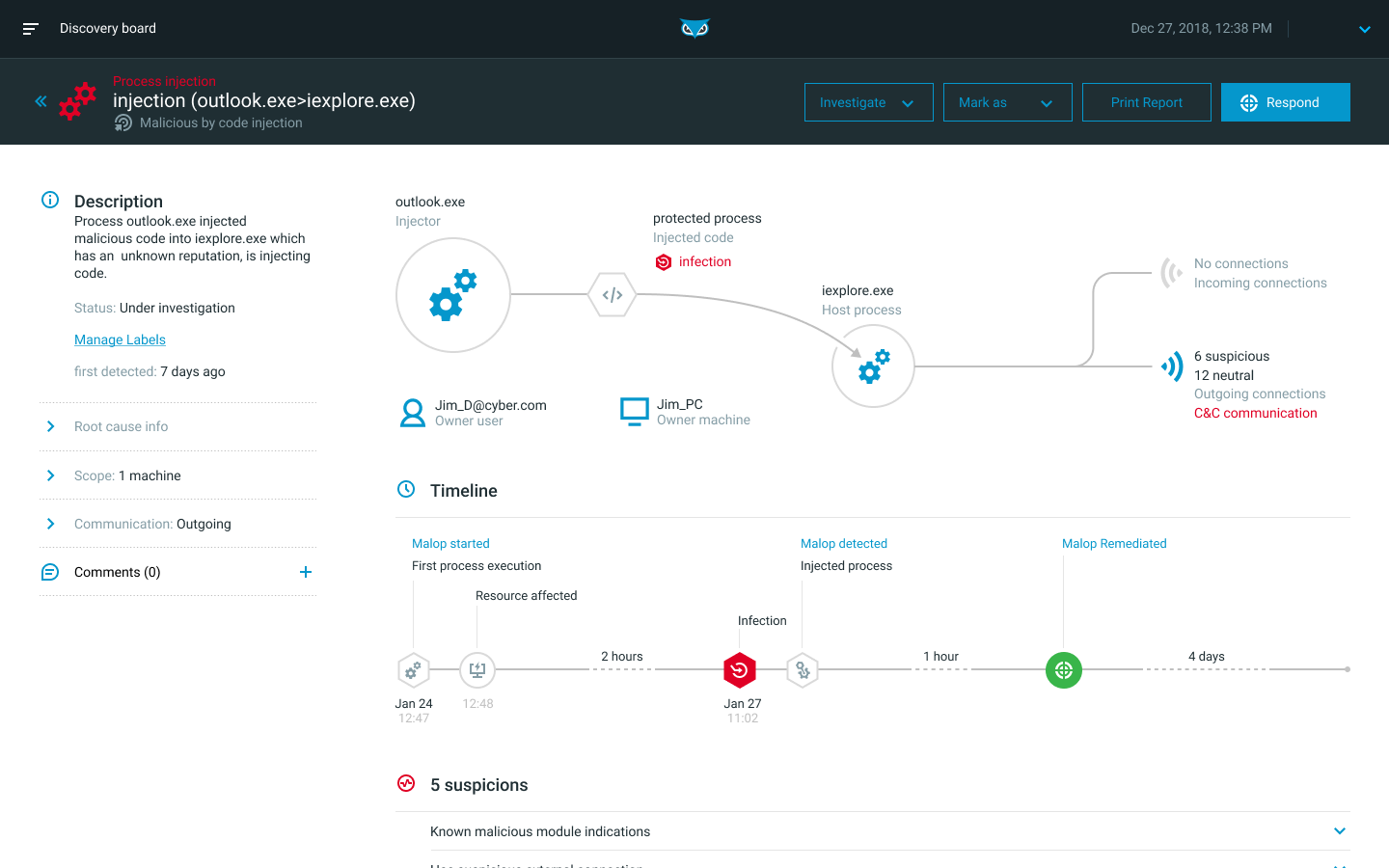
Cybereason Enterprise combines prevention and endpoint security controls with rapid detection to leverage contextual correlations across all endpoints in real time. It consolidates all intelligence about each attack into a single visual representation called a Malop (malicious operation).
Each Malop organizes the relevant attack data into an easy-to-read, interactive graphical interface, providing a complete timeline of the attack, the flow of malware across processes and users, and all incoming and outgoing communications for affected machines.
Netenrich works with small and midsize companies on right-sizing their security operations and driving their digital transformation efforts. Its XDR services enable continuous, full visibility and coverage across all network assets and hybrid cloud environments.
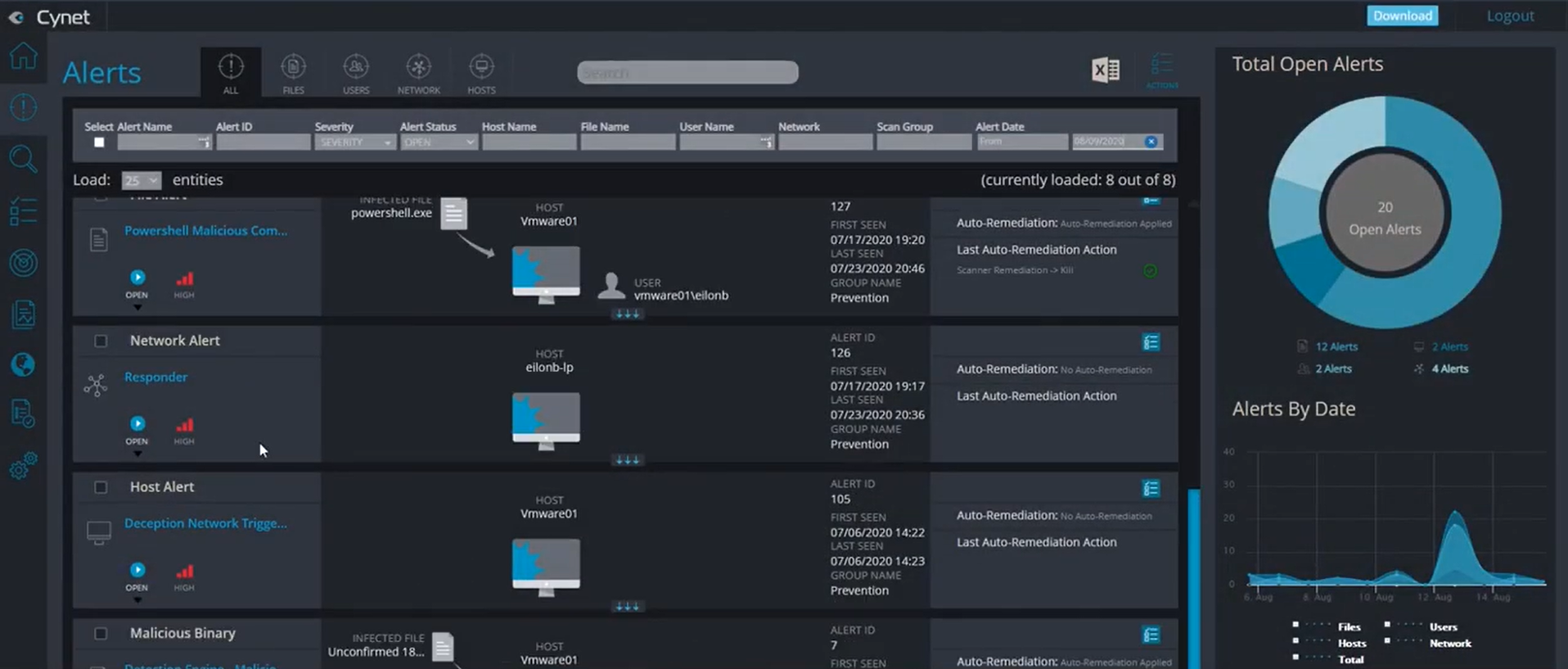
Cynet XDR prevents and detects threats on endpoints, networks, and users. For each identified threat, it triggers an automated investigation flow that reveals the attack’s scope and root cause, and applies automated remediation. It works in conjunction with CyOps, Cynet’s 24/7 SOC team of threat researchers and security analysts.
EDR tools vary from vendor to vendor. Most incorporate antivirus tools. Others offer a blend of functions such as machine learning, behavioral analysis, threat monitoring, detection of indicators of compromise (IoC), and ransomware protection.
A great many vendors and Managed Service Providers (MSPs) are now offering EDR. EDR is available on-premises, in the cloud, as a hybrid solution, or as a purely managed service. When fully managed, the EDR software is often called MDR. Some vendors add advanced functions, calling the service XDR.
Generally speaking, most EDR software provides a majority of these functions:
Depending on your organization’s needs, it may be beneficial to opt for a managed detection and response service. With MDR, it is important to determine whether the technology used by the operators is included in the price of the service. Some will require you to purchase your own tools (such as EDR software) separately. Others will offer the full technology stack in addition to the services component. Ideally, an organization should be able to share its endpoint and network data with the MDR provider.
Further, MDR offerings need granular real-time endpoint visibility to catch and stop modern attackers. Above all, you need expertise from an MDR provider. How big is the service? How many attacks have they stopped? You want to be backed by a team who has the experience to not only detect an attack, but also the ability to quickly investigate and respond.
Property of TechnologyAdvice. © 2026 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.