by Dan DiNicolo
http://www.2000trainers.com
While connecting to the Internet may seem innocent enough, users and administrators still need to take steps to ensure that their connections are secure. Dan Dinicolo’s latest article discusses the Windows XP built-in Internet Connection Firewall (ICF) tool and how it works to keep the bad guys out while allowing you to surf in peace.
The Internet is both a
wonderful resource and a very dangerous place. While connecting to the
Internet may seem innocent enough, you still need to take steps to ensure
that your connection is secure. This doesn’t just apply to people with fancy
broadband connections either. Every day, hundreds of people roam the
Internet using a variety of utilities, doing nothing more than scanning
ranges of IP addresses looking for unprotected systems. If you’re connecting
to the Internet from a system running Windows XP, security just got easier
thanks to the included Internet Connection Firewall (ICF).
If you think that nobody
would ever want to hack into your particular system, you’re probably right.
But that’s not the point. A variety of easy-to-use tools are available to
what are known as “script kiddies”. Essentially, these are folks with a
limited knowledge of hacking who are using pre-built tools to attempt to
gain access to Internet-connected systems. While they may not care about you
specifically, what they’re usually after is the ability to connect to your
PC, potentially take control of it, and even just root around through your
files a little. Furthermore, it doesn’t matter whether you’re using a
dial-up or broadband connection. While a high-speed connection may be a
better (and easier) target, everyone connected faces a risk. On any given
day, I check my log files and find between 10 and 15 connection attempts to
my PC from outside users.
Again, almost none of the
people are probably targeting me specifically. Instead, they are usually
running a program known as a port scanner, which will scan ranges of IP
addresses looking for open ports. An open port is created by a network
application waiting for a connection. For example, you might be running a
web or FTP server on your PC, or you may have unknowingly installed a Trojan
horse program by opening an email attachment that somebody sent you. Of
course, there may be nothing of interest running on your PC. But, when one
of these script kiddies does find an open port, the next step is trying to
connect to it — maybe they’ll get access to your system, and maybe they
won’t. Understand that there are literally hundreds of programs designed to
give even the novice user a way to hack into your PC. When all is said and
done, it’s up to you to try and stop them.
Internet Connection Firewall
Systems running Windows XP
include a new feature referred to as the Internet Connection Firewall. This
tool is both easy to use and to configure. There really is no need to go out
and purchase a more powerful tool unless you require more extensive
reporting and want all kinds of fancy notification options. For the majority
of users, Internet Connection Firewall will meet their basic need — keeping
the bad guys out, while allowing them to surf in peace.
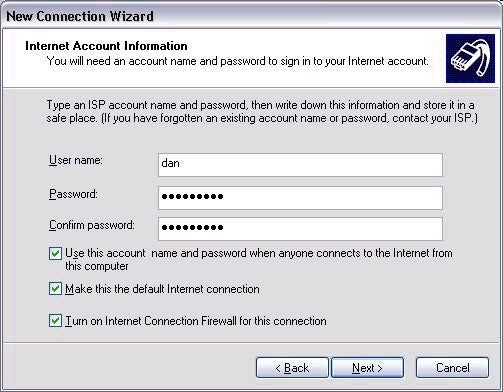
Configuring the Internet
Connection Firewall can be as easy as clicking a single button when setting
up your Internet connection using the New Connection Wizard. The checkbox is
found at the bottom of the screen, as shown below. By default, ICF will
block any and all connection attempts from the outside world. That is,
you’ll be allowed to access the Internet as normal, but any connection
attempts originating from the Internet will automatically be denied. If that
doesn’t sound like a bad default, you’re right. However, it’s also possible
that you will need a little more flexibility in your environment.
Whether or not you chose to
enable ICF when originally configuring your Internet connection doesn’t
matter. You can always access ICF settings by right clicking on the icon for
your Internet connection in the Network Connections program and choosing
properties. Enabling or disabling ICF is accomplished via the checkbox at
the top of the Advanced tab. If you want to delve a little deeper into ICF’s
capabilities, you’ll need to first enable ICF and then press the Settings
button in the lower right.
While the default
configuration provides great security, it’s also possible that you require
some users to connect to your system(s) from the outside world. For example,
you may have your system configured as an FTP server, or potentially as a
VPN server to give you access to your files while you’re on the road. The
defaults won’t work for you here, since all connection requests will be
denied. Instead, you’ll need to configure ICF to allow certain requests to
get through. This is accomplished using the Services tab in the ICF
settings.
The list of available
services shown below is decidedly short. Only the most common Internet
services are defined. If these meet your needs, simply check the boxes
associated with those services, and ICF will allow these connections
through. If you need to provide access to a service not found on this list,
you have a little more work ahead of you.
All applications wait for
incoming connections on port numbers. These are usually pre-assigned to
applications based on Internet standards. The first step in allowing access
to an application (such as a web server) from the Internet is finding out
the port number it uses to handle requests. For a web server, this is TCP
port 80 by default. For other services the port number will vary, but
usually it can be found in a program’s documentation. Then, you simply set
up a new entry on the Services list that includes a name and the associated
port number.
Unlike many popular home
firewall products, ICF will not bother you with annoying pop-up messages
every time somebody attempts to scan your system. Again, remember that most
people aren’t attempting to access your system, but rather a range of
systems according to IP addresses. If ICF is configured to not allow any
connections from the Internet, outside users won’t see any open ports on
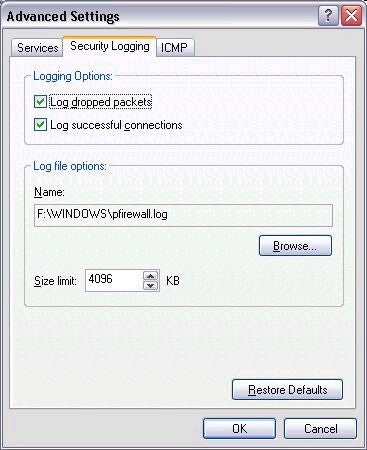
your system, so being notified shouldn’t be an issue. However, all
connection attempts should still be logged, as shown above. If enabled,
connection attempts will be written to a file called pfirewall.log in your
Windows directory. It’s generally a good idea to check this file at least
once in a while, just to get a sense for who is trying to connect to your
system and when.
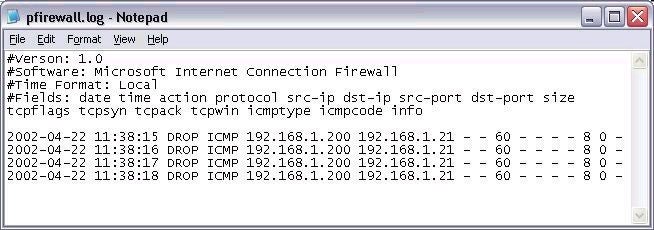
Finally, you can also
control how your system responds to certain ICMP diagnostic messages, such
as a ping request. Again, you have control over whether or not your system
will respond. If ICF is enabled, your system will not respond to ICMP
messages. In other words, if somebody pings you, your system won’t provide a
reply. If they don’t get a reply, they’ll probably assume that the IP
address isn’t valid or connected. In both cases, this is good news for you.
However, you may want to enable responses or other messages for your system.
If so, you can enable them individually from the ICMP tab in the ICF
settings. The log file shown below shows an attempted ping from system
192.168.1.200 that was dropped by my ICF protected system.
The Internet Connection
Firewall is a step in the right direction for Microsoft. While it’s only
included with Windows XP at present, you can expect it to be part of all
future versions as well. Whether you’re using a dial-up or broadband
connection, it’s in your best interests to keep ICF enabled for all
connections.
Dan
http://www.2000trainers.com

