Active Directory provides authentication and authorization services. A healthy Active Directory environment keeps all other services running effectively.
In our earlier Active Directory Health Check Server Tutorial, we explained two important health check items: “Active Directory Replication Topology” and “Subnets Not Associated with AD Sites.” We covered the benefits of using Hub-Spoke Replication Topology as opposed to Mesh Topology and provided a PowerShell script you could use to collect the number of AD Sites associated with each AD Site Link.
In today’s Server Tutorial  we are going to explain why it’s necessary to reboot production domain controllers once a month and how you can use a PowerShell script provided in this tutorial to collect domain controllers uptime information.
we are going to explain why it’s necessary to reboot production domain controllers once a month and how you can use a PowerShell script provided in this tutorial to collect domain controllers uptime information.
It is important to understand that since domain controllers are designed to provide critical authentication and authorization services, and domain controllers are busy all the time, domain controllers must be rebooted once a month or based upon your maintenance window that you have included in your standard health check processes.
Before we start explaining the domain controller uptime PowerShell script, let’s cover exactly why it is necessary to reboot domain controllers. Two important reasons that you should always take into consideration when deciding whether to reboot domain controllers or not are listed below:
- Memory Leak Issues: Memory leaks might occur in the Lsass.exe process. The Lsass.exe process running on domain controllers is responsible for providing authentication services to Active Directory clients.
Over time, memory leaks might affect performance of domain controllers. A large memory leak might result in unacceptable response times from the Lsass.exe process and high memory usages on the Operating System. To overcome memory leak issues, it is recommended to periodically reboot affected domain controllers.
Although new versions of Windows such as Server 2012 R2 and the upcoming Windows Server 2016 have been designed to recover from memory leak issues automatically, it is still recommended that you reboot affected domain controllers, which in turn might resolve other memory leaks issues that the OS is unable to resolve automatically.
- Most Security Updates Require a Reboot: It is important to note that a Windows server computer and the domain controllers require regular patching to ensure service packs, hotfixes, and security patch levels are consistent across all domain controllers.
Since security patches replace low-level DLL files in the Operating System, most of the security updates require a reboot before the security patches can be applied successfully. Note that Microsoft releases security patches every month, so it becomes imperative to reboot domain controllers monthly to apply the applicable patches.
With the above reasons for rebooting domain controllers in mind, here is a PowerShell script you can use to collect domain controller uptime information. This domain controller uptime script can help you identify the number of days since the last reboot for each domain controller.
Steps:
Change ITDynamicPacks.Net forest name to your Active Directory forest name.
Get a list of all domain controllers from Active Directory forest by executing the command below and storing output in C:TempDCList.TXT file:
DSQuery Server -o rdn > C:TempDCList.TXT
Copy the entire script below to a .PS1 file and execute from the PowerShell window.
$CurForestName="ITDynamicPacks.Net"
$TestCSVFile="C:TempDCUpTimeReport.CSV"
$GDCList="C:TempDCList.TXT"
$TotNo=0
$ItemCount=0
$TestText = "Please check result"
$TestStatus="Completed"
$SumVal = "NA"
$ErrorOrNot = "No"
$ThisString="Domain Controller, Up Time, Local Time, Time Zone, Days Not Rebooted, Status"
Add-Content "$TestCSVFile" $ThisString
$TodaysDate = Get-Date
Foreach ($ItemName in Get-Content "$GDCList")
{
$operatingSystem = Get-WmiObject Win32_OperatingSystem -ComputerName $ItemName
IF ($Error.count -ne 0)
{
$ThisSTR = $ItemName+",Error Connecting"
$ErrorOrNot = "Yes"
Add-Content "$TestCSVFile" $ThisStr
}
else
{
$RTime=[Management.ManagementDateTimeConverter]::ToDateTime($operatingSystem.LastBootUpTime)
$LocalTime=[Management.ManagementDateTimeConverter]::ToDateTime($operatingSystem.LocalDateTime)
$CurTimeZone=$operatingSystem.CurrentTimeZone
$StatusNow = ""
$R = $RTime
$Z = $TodaysDate
$DayNotRebooted = (New-TimeSpan -Start $R -End $Z).Days
IF ($DayNotRebooted -ge 30)
{
$StatusNow = "WARNING: Not rebooted since last 30 days"
}
$ThisStr=$ItemName+","+$RTime+","+$LocalTime+","+$CurTimeZone+","+$DayNotRebooted+","+$StatusNow
Add-Content "$TestCSVFile" $ThisStr
}
}
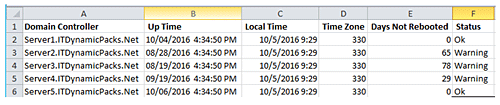
Once the script has finished executing for all domain controllers, a report will be generated in the DCUpTimeReport.CSV file in the C:Temp folder as shown in the screenshot below:
As you can see in the report above, the script collects uptime for each domain controller specified in the C:TempDCList.TXT file and reports how many days a domain controller has not been rebooted in the “Days Not Rebooted” column.
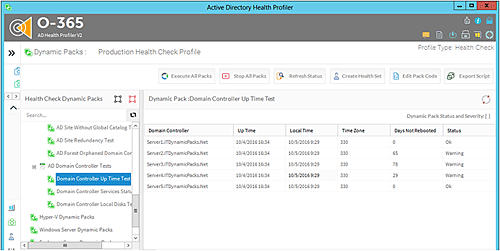
The above script is part of the “Domain Controllers Up-Time Test” Dynamic Pack that is available for use with the Active Directory Health Profiler. The “Domain Controllers Up-Time Test” Dynamic Pack can be executed for single or multiple Active Directory forests and you will be able to see the Dynamic Pack result in the Active Directory Health Profiler console as shown in the screenshot below:
Conclusion
We’ve detalied two key reasons for rebooting production domain controllers. The overall objective for rebooting production domain controllers is to ensure domain controllers can serve authentication and authorization requests in a timely manner and also to ensure domain controllers are as secure as possible with timely updates and security patches.
The domain controller uptime PowerShell script will help you maintain the health of your domain controllers by ensuring each domain controller has rebooted once a month and that you are following reboot maintenance processes regularly for domain controllers.
Nirmal Sharma is a MCSEx3, MCITP and Microsoft MVP in Directory Services. He specializes in directory services, Microsoft Azure, Failover clusters, Hyper-V, System Center and Exchange Servers, and has been involved with Microsoft technologies since 1994. In his spare time, he likes to help others and share some of his knowledge by writing tips and articles on various sites and contributing to Health Packs for ADHealthProf.ITDynamicPacks.Net solutions. Nirmal can be reached at [email protected].