Besides auditing, you’ll also
need to configure Message Queuing Service (this is included with Windows
2000 but is not usually installed by default) and create a dedicated user
account under which LANguard S.E.L.M. will run.
The installation process is very straightforward. In fact, most of the
configuration can be accomplished using the initial installation wizard.
This includes adding computers to be monitored, specifying whether a SQL or
Access database should be used, configuring mail server settings, and
specifying normal operation times. Once completed, settings can of course be
changed using the LANguard S.E.L.M. configuration tools.
LANguard S.E.L.M. adds a number of tools (many of which are MMC-based) for
managing and monitoring alerts and their settings. These include:
LANguard S.E.L.M. Configurator – used to configure program alerts,
rules, and settings.
LANguard S.E.L.M. Event Viewer – used to view categorized events,
similar to Event Viewer but in a more organized fashion.
LANguard S.E.L.M. Reporter – used to build standard or custom reports
that outline the result of security log analysis.
LANguard S.E.L.M. Troubleshooter – a wizard that can be used to
provide GFI with information on issues you are experiencing with the
product, to be forwarded in an e-mail to GFI.
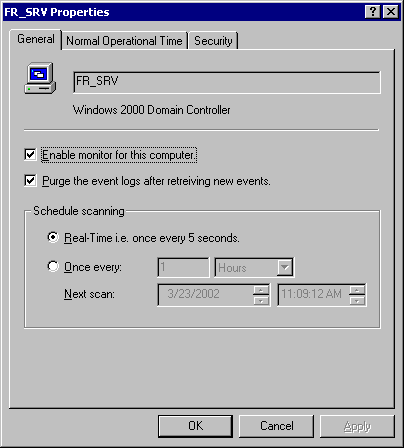
Additionally, the LANguard S.E.L.M. Monitor tool sits in the system tray,
providing information about the security log collection process on domain
computers. Since Event logs from different systems will have to be retrieved
by the system where the database resides, you can also specify how often
this happens for individual (or groups of) computers. For example, on
critical or high-risk servers you might specify that real-time monitoring
take place every 5 seconds. On lower risk computers, you might specify that
log collection occur every six hours. Striking a balance here is important,
since monitoring too aggressively may impact performance. This is yet
another reason why you should characterize network systems prior to
installation. The screenshot below outlines the monitoring settings for one
of my domain controllers.
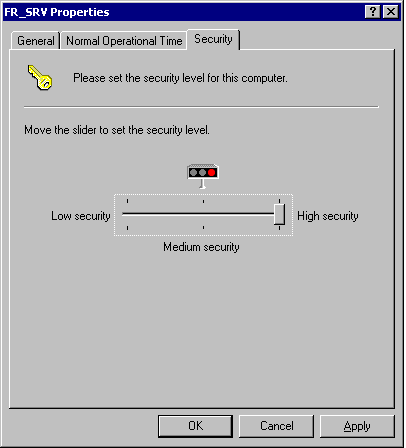
In order to account for the different levels
of security monitoring required on domain systems, LANguard S.E.L.M. allows
you to define the security level of individual systems, and set defaults.
For example, you could configure things such that individual servers have a
medium security setting by default, while domain controllers or critical
servers are set to high. You can later use these settings to define which
types of events are considered critical for a given system type.
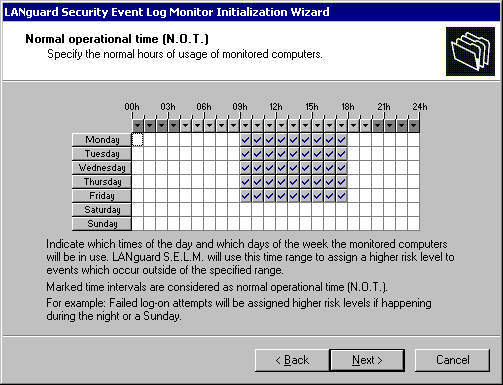
Another important feature is the ability to
define what is known as Normal Operation Time (N.O.T). This tells LANguard
S.E.L.M. which times are considered normal business hours. This feature
provides an even more granular level of control over how alerts are defined
– for example, a failed logon event during business hours might be
considered a medium security threat, and a high (or even critical) security
event after hours. The ability to control what is considered critical (and
when) is part of what makes LANguard S.E.L.M. such a powerful tool.