As a system admin, you may find yourself needing to regularly get Active Directory last logon date and times for your users. Tracking last logon date and times is an essential piece in gaining a holistic view of the activities of users. In this tutorial, we’ll cover a few methods for getting this information, including PowerShell commands and enterprise tools.
Reason for Tracking the Last Logon Date and Time
The main reason for tracking the last logon date and time for all users is to avoid any potential security risks by preventing unauthorized access to the network. This information makes it easy for System Administrators to identify inactive accounts and disable them from the directory. When these stale accounts remain active, attackers can retrieve and use those credentials to log on to any machine and gain access to the Active Directory environment.
How to Get the Last Logon for a Single User with Active Directory Users and Computers (ADUC)
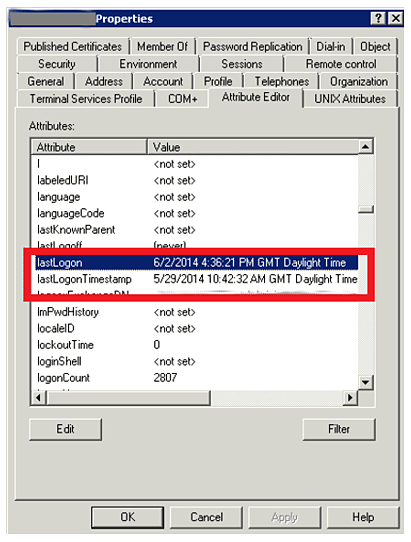
 The first method we’ll cover for how to get the last logon for a single user is with Active Directory Users and Computers (ADUC). ADUC stores the last logon date and time for a user in the LastLogonTimeStamp property. If you need to see the last logon date and time for a single user using the graphical user interface (GUI), you can use the ADUC tool. From the ADUC tool, right-click on a user, click on Property action, switch to the Attribute Editor tab and then search for the “LastLogonTimeStamp” property as it is shown in the screenshot below:
The first method we’ll cover for how to get the last logon for a single user is with Active Directory Users and Computers (ADUC). ADUC stores the last logon date and time for a user in the LastLogonTimeStamp property. If you need to see the last logon date and time for a single user using the graphical user interface (GUI), you can use the ADUC tool. From the ADUC tool, right-click on a user, click on Property action, switch to the Attribute Editor tab and then search for the “LastLogonTimeStamp” property as it is shown in the screenshot below:
How to Get the Last Logon Date and Time Using PowerShell
Next, we’ll cover how to get the last logon date and time using PowerShell commands. While the ADUC tool can be handy if you are investigating the last logon time for a single or a just few users, in many cases you’ll need to collect the last logon information for every Active Directory (AD) user to help you understand logon activity for all AD users. Since AD stores this information in the LastLogonTimeStamp attribute, it can be queried using simple PowerShell commands as explained below.
How to Get Last Logon Date and Time for a Single user with PowerShell
To get last logon date and time for a single user with PowerShell, execute the below commands:
$UserName = "David.Das"
Get-ADUser $UserName -Properties LastLogonTimeStamp
When you run the above PowerShell commands, you will see the last logon time stamp for user “David.Das.”
How to Get Last Logon for All Users with PowerShell
If you wish to collect the last logon date and time for all users with PowerShell and store the output in a CSV file for reporting purposes, you can execute the following PowerShell script:
$ReportFile = "C:TempLastLogonTimeStampUsers.CSV"
Remove-Item $ReportFile -ErrorAction SilentlyContinue
Get-ADUser -Filter * -SearchBase "OU=,DC=ServerWatch,DC=Com" -ResultPageSize 0 -Properties CN, LastLogonTimeStamp | Select CN, @{R="LastLogonDate"; F={[DateTime]::FromFileTime($_.LastLogonTimeStamp)}} | Export-CSV $ReportFile -NoTypeInformation
How to Audit Last Logon By Organizational Unit (OU)
When reporting this information, it helps to know how to audit the last logon by organizational unit so that you can more clearly track the activity of groups of users across the company. Note that the third PowerShell command in the above script converts the date and time returned for every AD user using the “DateTime” function and then exports the output to a CSV file referenced by the $ReportFile variable. It is important to understand that you might have several organizational units (OU) created in Active Directory that hold users for different departments.
For example, you might have created an organizational unit by the name “SalesUsers,” which only stores users for the sales team and another OU with the name “FinanceUsers,” which stores users for the finance team. The above PowerShell script can only be used to query the last logon activity for users in a single OU specified in the “-SearchBase” parameter.
How to Audit Organizational Units with Powershell
If you wish to collect the last logon activity for users in each department OU and have the output stored in a separate CSV file for each department OU, you can create a text file that includes the list of OU names and then make use of a PowerShell “ForEach” loop.
How to Audit Organizational Units with Netwrix Auditor
Another option is to audit organizational units with Netwrix Auditor for Active Directory, which solves user auditing problems by letting you create plans for each department’s OU. For example, you can create a plan that collects the last logon date and time for users in Sales OU and another plan to collect the same information for users residing in Finance OU.
Once these plans have been created, Netwrix Auditor can execute the plans and have the reports sent to you via email. You can also check the last logon date and time information for users by opening the Netwrix Auditor console as it’s shown in the screenshot below:
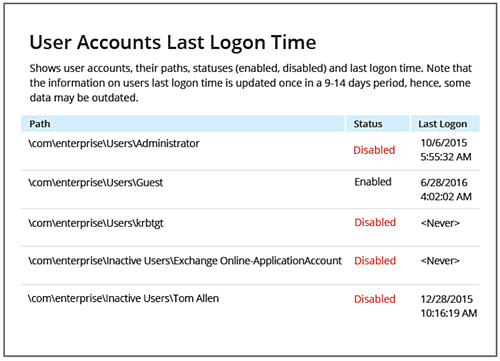
Note that you may not want users to remain enabled if the users have not logged onto the Active Directory for a long time. That’s why in addition to displaying the last logon date and time of AD users, Netwrix Auditor also displays the status of each user as shown in the screenshot above.
Tips for Getting Last Logon Date and Time
In this Server Tutorial, we provided simple PowerShell commands and a script to collect the last logon time and date for Active Directory users. While you can use PowerShell to collect the required information, it is recommended that you use an enterprise tool like Netwrix Auditor for Active Directory, which can help you create auditing plans based on your requirements and collect the data automatically.
Nirmal Sharma is a MCSEx3, MCITP and Microsoft MVP in Directory Services. He specializes in directory services, Microsoft Azure, Failover clusters, Hyper-V, System Center and Exchange Servers, and has been involved with Microsoft technologies since 1994. In his spare time, he likes to help others and share some of his knowledge by writing tips and articles on various sites and contributing to Health Packs for ADHealthProf.ITDynamicPacks.Net solutions. Nirmal can be reached at [email protected].

