Policies
Policies form the basis on environment and security configuration in Windows 2000. In very broad terms, two types of policies exist – Local Policy (which is set on an individual computer) and Group Policy (which can be applied to multiple computers and users according to settings in Active Directory). Without Active Directory, only Local Policies can be applied. First well look at Local Policies, followed by an introduction to Group Policy.
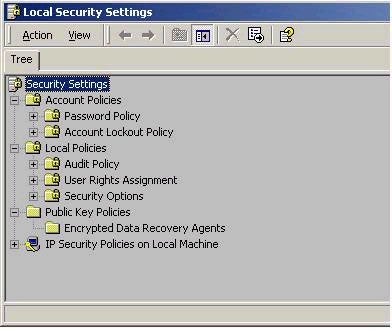
Local security policy controls security-related settings on an individual Windows 2000 system. Settings found in the Local Security Settings tool relate to three major areas – Account Policy, Local Policy, and Public Key Policy, as shown below:
Account Policies control settings such as password policy (password uniqueness, age, etc) and account lockout policy (lockout threshold, duration, etc) for local accounts. That is, these settings only apply to accounts contained within the systems Security Accounts manager (SAM) database, and not to domain accounts.
Local Policies contains settings relating to the Audit policy on the local system, the assignment of user rights, and security options. Audit Policy includes options for types of events you wish to audit, such a file and object access over this particular system. User Rights assignment is where you would give users or groups rights to perform system tasks, such as the right to change system time, or the right to back up files and folders. Note that this is different that in NT 4.0, where rights were given using the User Manager tool. The Security Options section of Local Policies allows you to control security-sensitive settings on the local machine, such as disabling the Ctrl+Alt+Del requirement for logon, clearing the pagefile on shutdown, and so forth. An example on some user rights settings is shown below:
Public Key Policies in the Local Security Settings tool allow you to set the EFS recovery agent, which by default will be the local administrator account.
Although local policy settings give you a strong degree of control, they are still fairly inflexible in that they must be configured locally on each machine. Note that it is possible to export policy settings to a file, and then import those local settings on to another system. Windows 2000 also includes a snap-in called Security Configuration and Analysis. This tool allows you to save policy settings to a database file, and then compare changes to security settings against this database. It is a useful tool in determining the impact that a change to a policy setting will have. This tool also allows you to save the database to a template file
(.inf file), which can then be applied to other systems. For more details about the Security Configuration and Analysis tool,
click
here.
In an Active Directory environment, policy settings are more easily applied using Group Policy. Group Policy is a more effective tool because it allows you to centralize the application of policy. Group Policies can be applied at 3 different levels in Active Directory: site, domain, and organizational unit (OU). Group policies allow you to configure all kinds of settings relating to the user and computer environment, such as removing the Run command or forcing certain wallpaper. They also include the security settings we discussed in Local policy. A deeper look at setting areas will be looked at in the Server portion of the series.
Although we haven’t yet really discussed Active Directory in the series, a brief overview will suffice for now. A site is a physical location in Active Directory. Any policies applied to a site will apply to all users in that site, regardless of the domain or OU they are a part of. A domain is still very similar to what you remember from NT 4. Any policy applied to a domain will affect all users and computers in the domain. Finally, an Organizational Unit, or OU, is a smaller container within a domain that represents breakdown for the purpose of administration or organization of objects (such as users and computers). Any group policy applied to an OU will affect users in that OU, as well as any sub-OUs (since OUs can be nested).
Since Group Policy can be set at different levels, it is possible that settings at one level (like site) could conflict with settings at another (like OU). As such, it is important to understand the order in which group policy gets processed. The order is:
Local Policy – Site – Domain – OU
What that means is very important, and you must understand it. Imagine you are a member of an OU called Sales in a site called Tallinn. All group policy settings merge together. That is, if a Tallinn site-level policy says you get green wallpaper, and a Sales OU-level policy removes the Run command, you will end up with green wallpaper and no Run command. However, if there is a conflict, the settings applied later will take precedence. Imaging the Tallinn site policy removed the Run command, and the Sales OU policy enabled it – you would end up having the Run command, since OU policy is applied after the site policy. Note that logging off and back on isn’t necessary in order to obtain the vast majority of group policy settings in Windows 2000. Group policy settings are automatically updated on the client system every 90 minutes by default (with a 30 minute offset). There is much more to Group Policy than just what has been discussed here – a more detailed look at group policy will follow in the Server portion of the series.